Protection for Retail APIs & Web Apps
ThreatX takes a protection-first approach to securing the APIs and applications that drive online storefronts, customer accounts, and online payment systems.
Securing Online Storefronts From Sophisticated Attacks to Ensure Availability
Retail organizations are challenged to meet the growing demands of online shopping and secure transactions that include consumers’ sensitive data. The 2020 COVID-19 pandemic may have locked down consumers to their households but it catapulted the shift to online buying. This shift of buying behaviors resulted in retail organizations needing to pivot business strategies – as we learned from a global retail customer:
“ After the 2020 lockdowns, everything became bigger and harder to manage. Everyday shopping traffic was up 43%. Flash sales, holiday shopping, and product launches were constantly setting record highs of traffic surges and our infrastructure wasn’t prepared to handle this overnight shift. Now, pile on top of that the responsibility to protect all of those consumers’ data from attackers. Our teams felt like we were drowning. ”
After deploying ThreatX, the team saw the full spectrum of attacks that were being identified with the solution’s behavior based approach. But what truly convinced them to move forward was the ThreatX Managed SOC, which helped to offload Tier 1 and Tier 2 tasks.
Solutions


Secure Consumer Online Shopping and Payments
Protect your consumers’ sensitive data with real-time detection and blocking against API abuse and web app attacks.
It’s great to build APIs and web applications from the bottom up, but that’s not always a scalable option, specifically for retail organizations struggling to meet the demands of online shoppers. Integrating open source APIs and micro-services to meet business needs makes defending your application perimeter more of a challenge. Full spectrum protection for your layer 7 traffic is really hard – but that’s what’s required to defend against modern attacks.
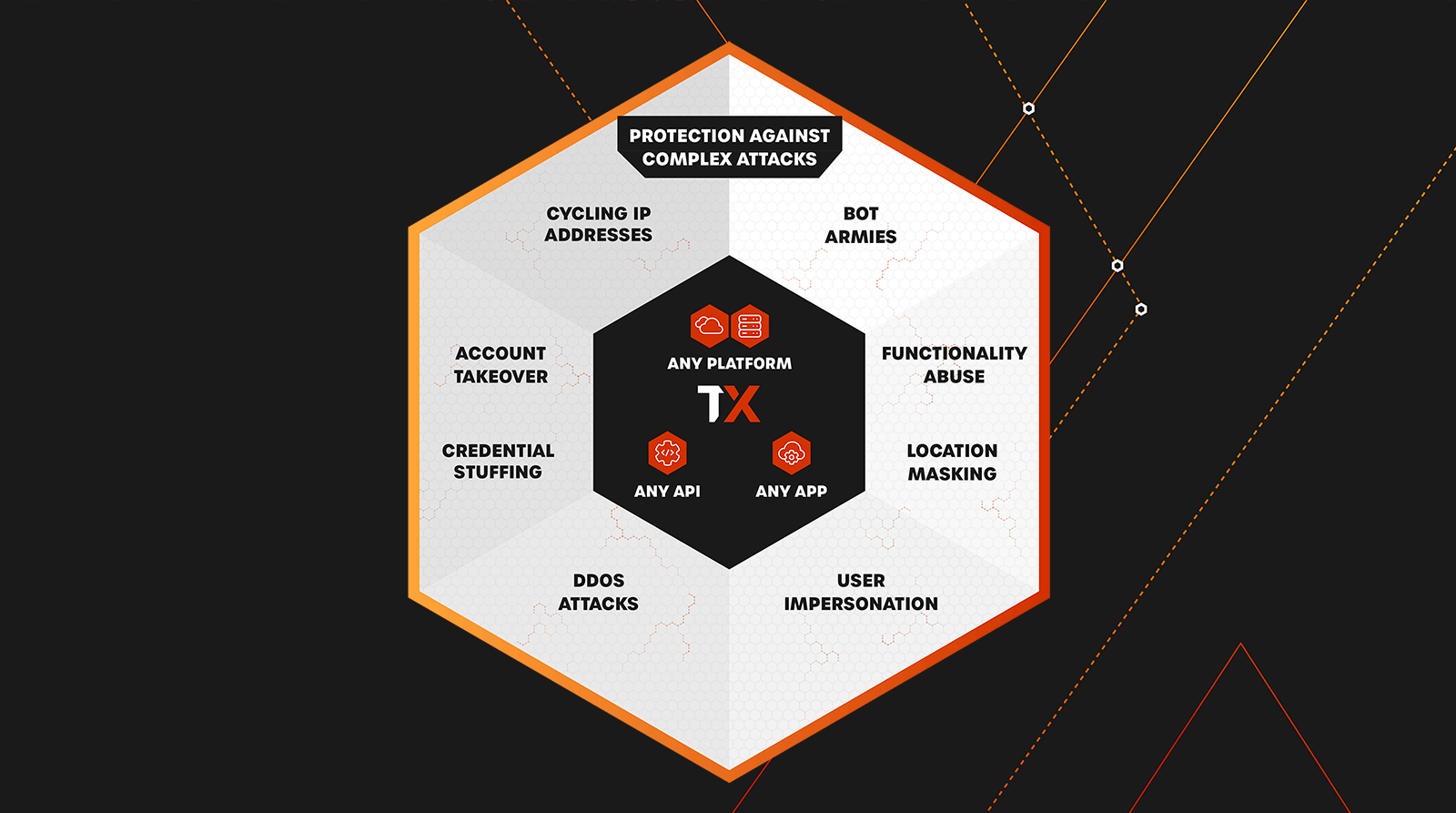
ThreatX protects our customers from threats like:
- Credential stuffing
- DDoS attacks
- OWASP Top 10 threats
- API abuse
- Botnets and bot armies
- Account takeovers
- SQL injection
- Zero day vulnerabilities
Find out more about how ThreatX protects customers’ sensitive data while ensuring platform availability by checking out ThreatX’s real-time blocking capabilities.

Prevent Fraud Activity and Account Takeover
Behavior-based blocking ensures that threats are blocked while maintaining low false positives and preventing legitimate users from ever being locked out.
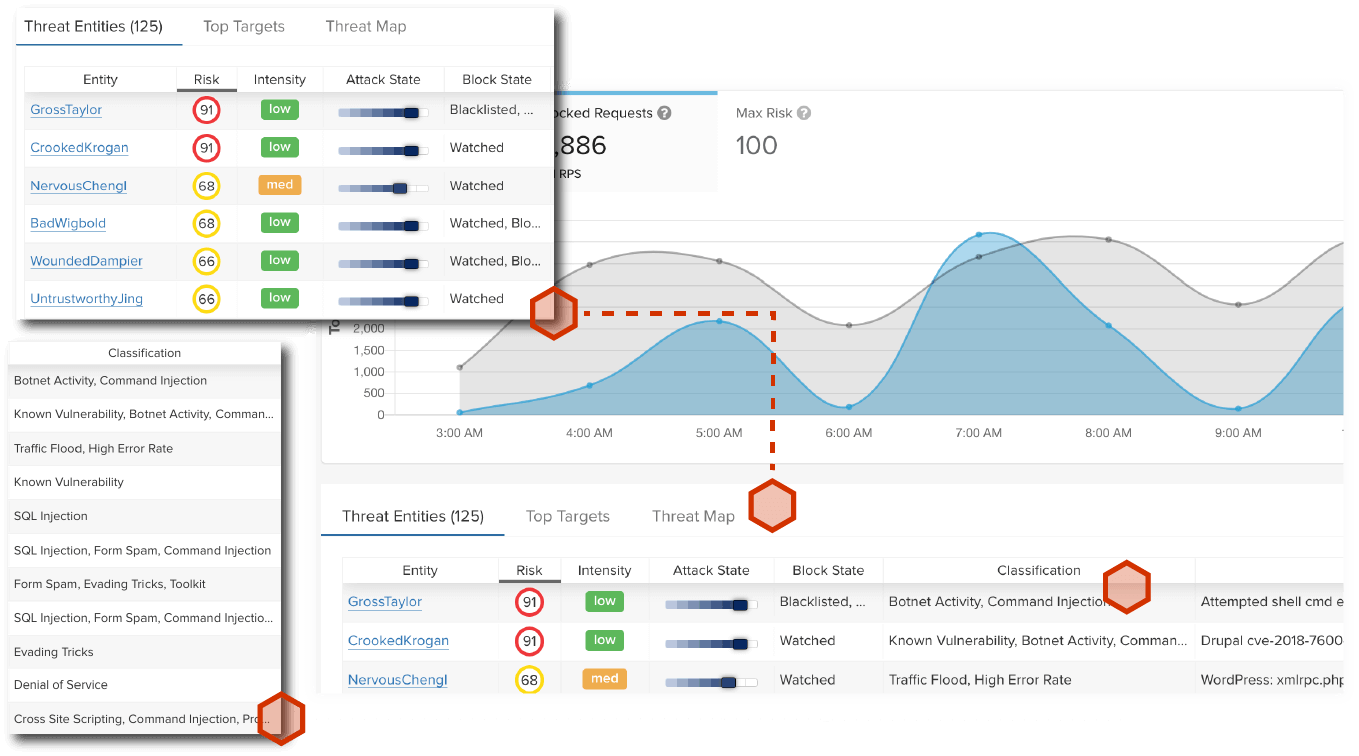
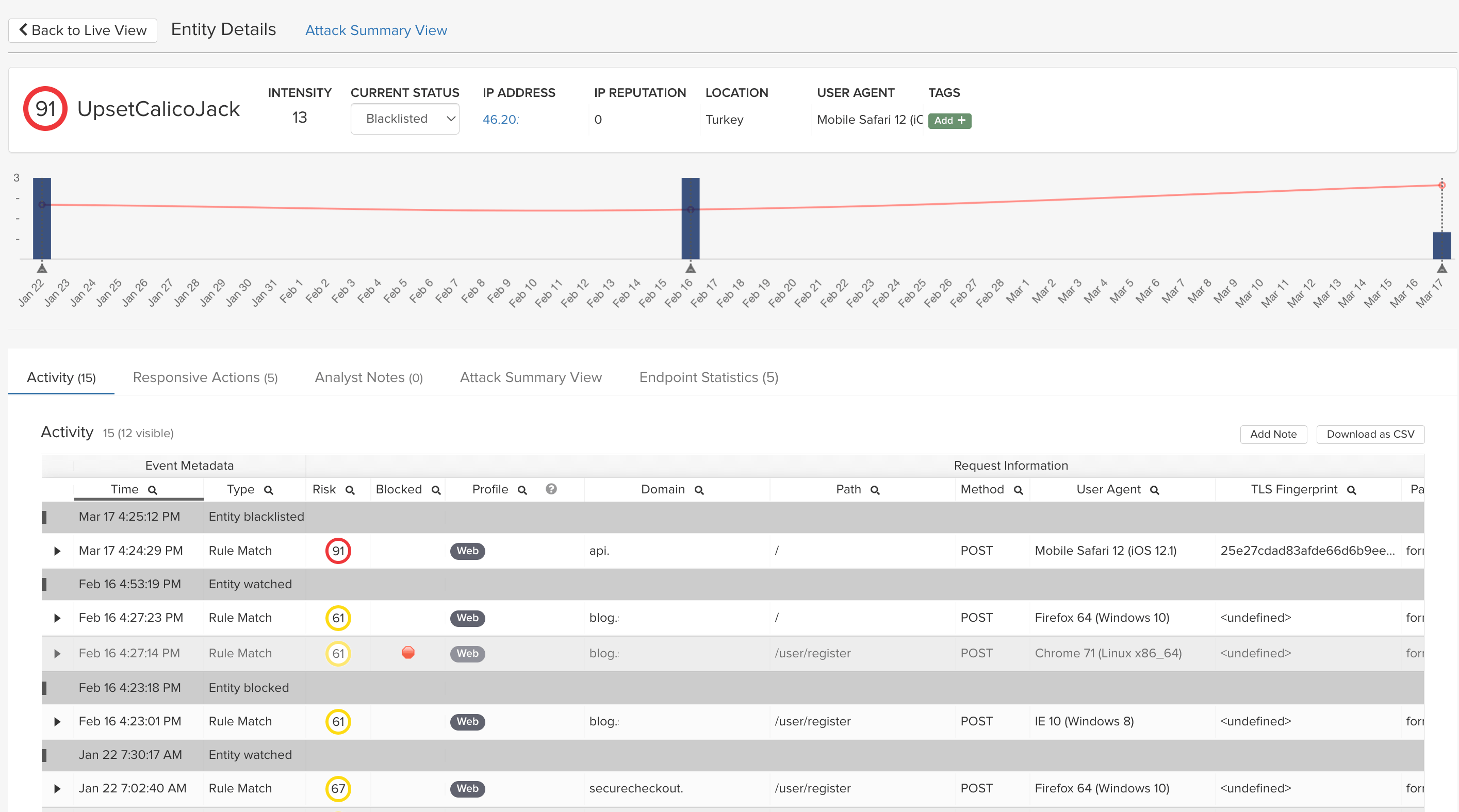
ThreatX goes far beyond signatures and anomaly detection with behavior-based analytics to identify and track malicious entities even as traits such as IP addresses and user agents change. This lets us track a complete picture of an entity’s attack attempts and risk so that enforcement is both highly accurate and laser-focused on what matters the most.
The benefits of this approach include:
- Fewer false-positives
- Fewer custom rules
- Less time managing and mitigating rule conflicts
- Less time spent documenting rulesets
- Less resource requirements when FTEs change over
Learn more about our single risk engine or our attacker-centric behavioral analytics.

Detect and Block Malicious Bots
Comprehensive coverage that scales against large, volumetric botnet attacks.
ThreatX provides visibility on bot-based attacks by using application profiling, IP interrogation, entity fingerprinting, and risk attribution to distinguish if malicious requests are being customized from a sophisticated attacker or automated by a distributed botnet. This combination of bot detection techniques and application intensity analysis means ThreatX can reveal a wide range of automated attacks such as ATO, credential stuffing, reputation attacks, and more.
Get comprehensive protection against:
- Brute force attempts
- TCP attacks
- HTTP flooding
- Spoofing
- Ping of death
- Smurf
- Teardrop
- Zero-Day DDoS attacks, and more…
Check out ThreatX’s approach to DDoS Protection & Bot Management.

Ensure Platform Availability and Reliability
Protection for online storefronts, mobile applications, and APIs that scales
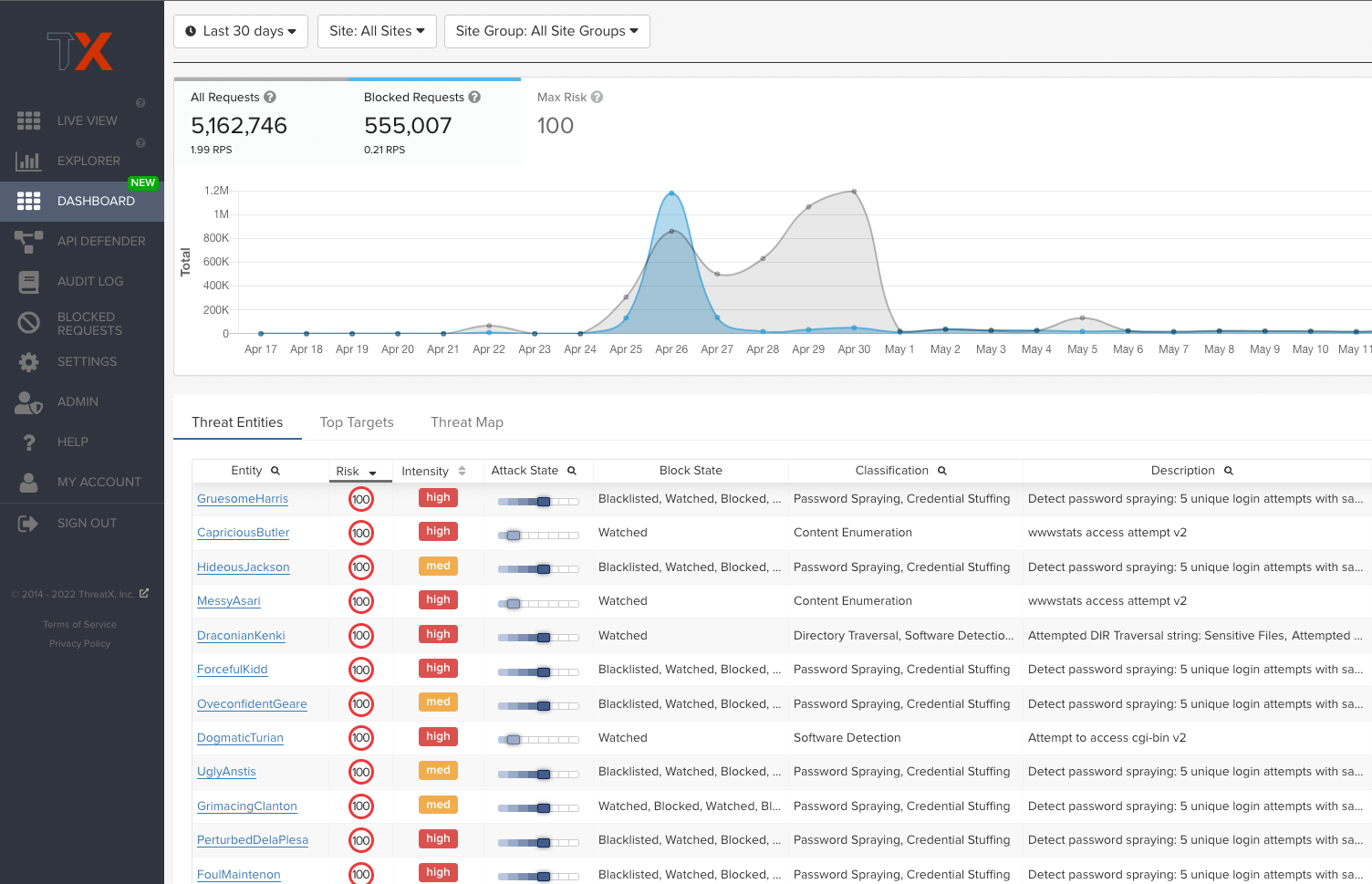
Large-scale events such as distributed denial of service (DDoS) attacks or even seasonal shopping, flash sales, and product promotions can lead to site outages without proper protection and resource scalability. Providing a seamless shopping experience has never been more important for retail and e-commerce organizations as consumers’ buying habits shift to online storefronts. ThreatX’s behavior-based approach identifies and blocks attackers in real-time, ensuring platform and product availability doesn’t get gobbled up by retail bots.
ThreatX provides platform reliability by:
- Preventing outages from large-scale, bot-based attacks like distributed DDoS
- Identifying and blocking credential stuffing attempts from accessing user accounts
- Managing traffic spikes with rate limiting and tarpitting
Learn more about ThreatX’s architecture at How it Works.

Meet Compliance Requirements With Ease
Secure all systems that manage your customers’ personal identifiable and payment data while reducing the burden of maintaining compliance.
ThreatX helps you meet PCI and GDPR requirements, but also improves the overall security of APIs and applications that manage sensitive customer data while reducing the burden of maintaining compliance.
ThreatX helps you meet the following PCI requirements:
- Requirement 6: Develop and Maintain Secure Systems and Software
- Requirement 1: Install and Maintain Network Security Controls
- Requirement 5: Protect All Systems and Networks from Malicious Software
- Requirement 10: Log and Monitor All Access to System Components and Cardholder Data

A Unified API & Web Application Protection Platform
Secure the APIs and Web Apps That Manage Financial Transactions

