Looking for a Managed Web Application Firewall You Can Set and Forget?
A cloud native, next gen managed WAF designed to simplify protecting multi-cloud environments against sophisticated security threats.
- Set it and forget it threat protection
- Protect APIs & applications against DDoS, botnets, and more
- On-board sites in minutes
- Fully-managed, with 24/7 support
Out-of-the-box protection for all your APIs and applications, fully managed with 24/7 support, so you can sleep better at night.
How We Help
Risk-Based Blocking
Confidently block malicious traffic without the worry of false positives
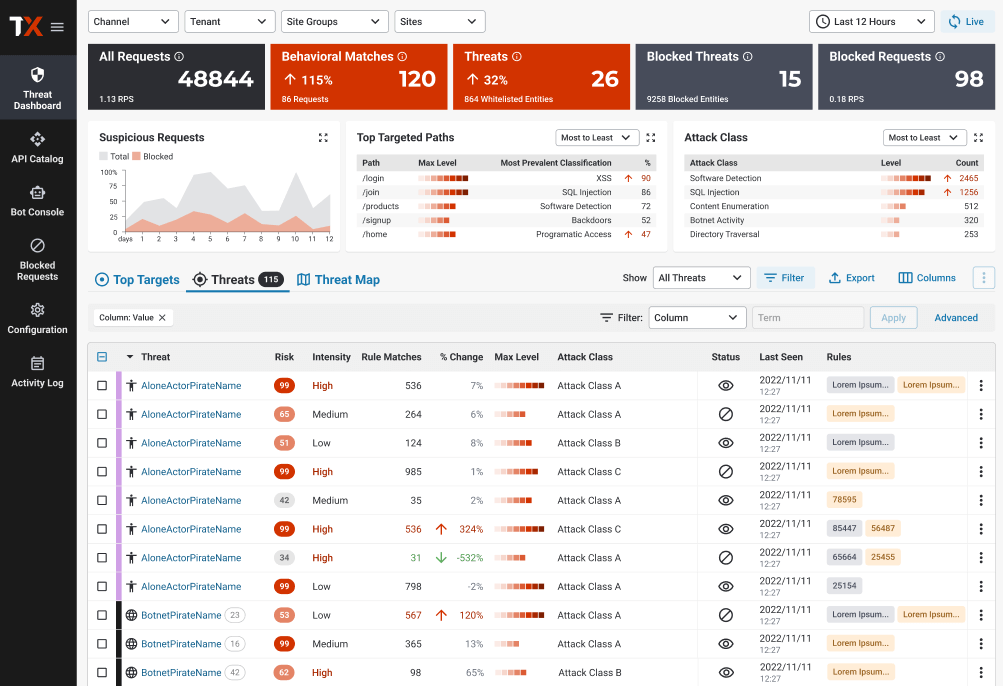
False positives are the bane of any security tool. For a WAF, that translates to blocking legitimate traffic and users, causing not only inconvenience but also potentially lost revenue. Risk-based blocking will help you identify and block only high-confidence threats that pose the most serious risks, giving you protection in depth that just works. While risk-based blocking is the choice of most customers, manual and request-based alternatives are also available.
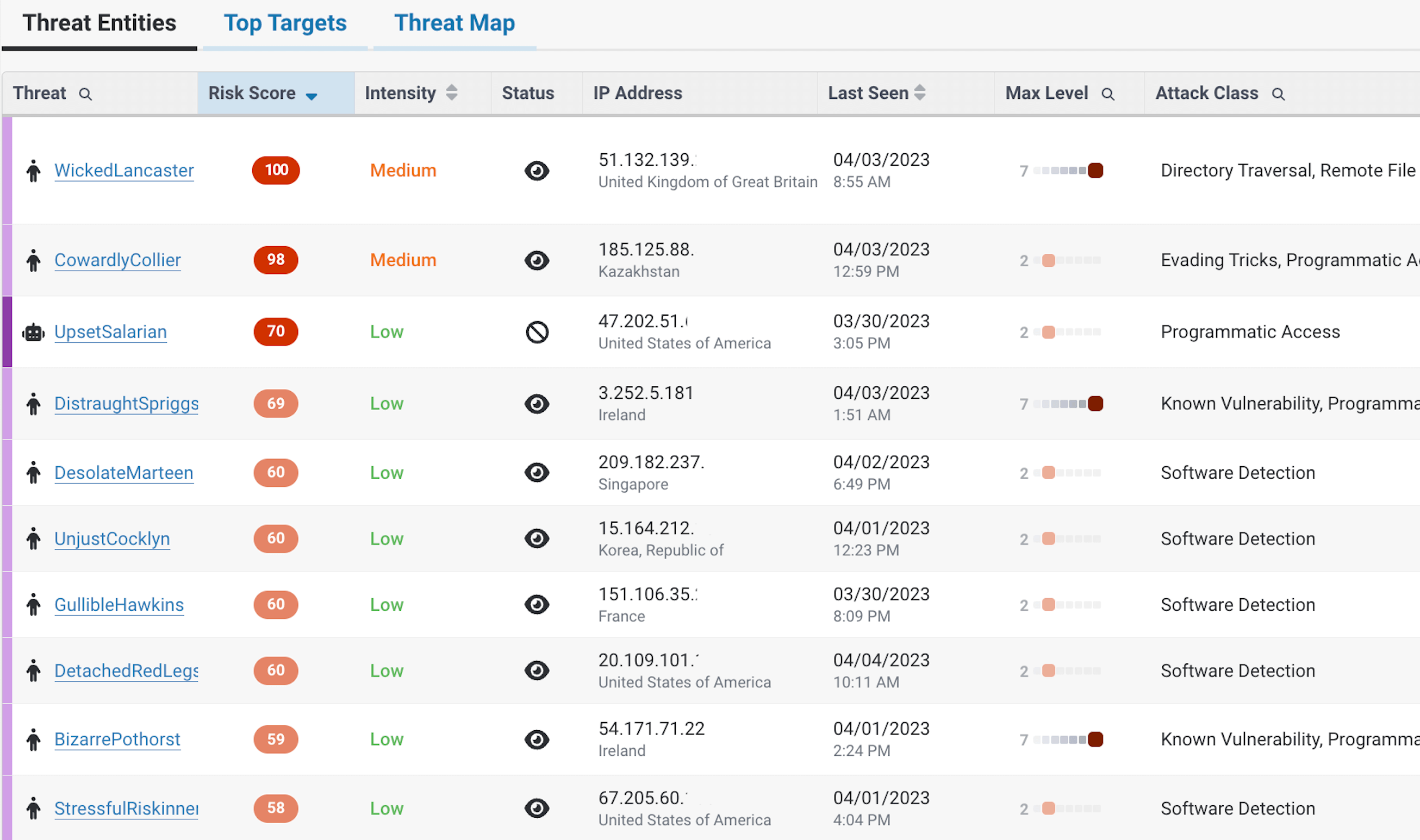
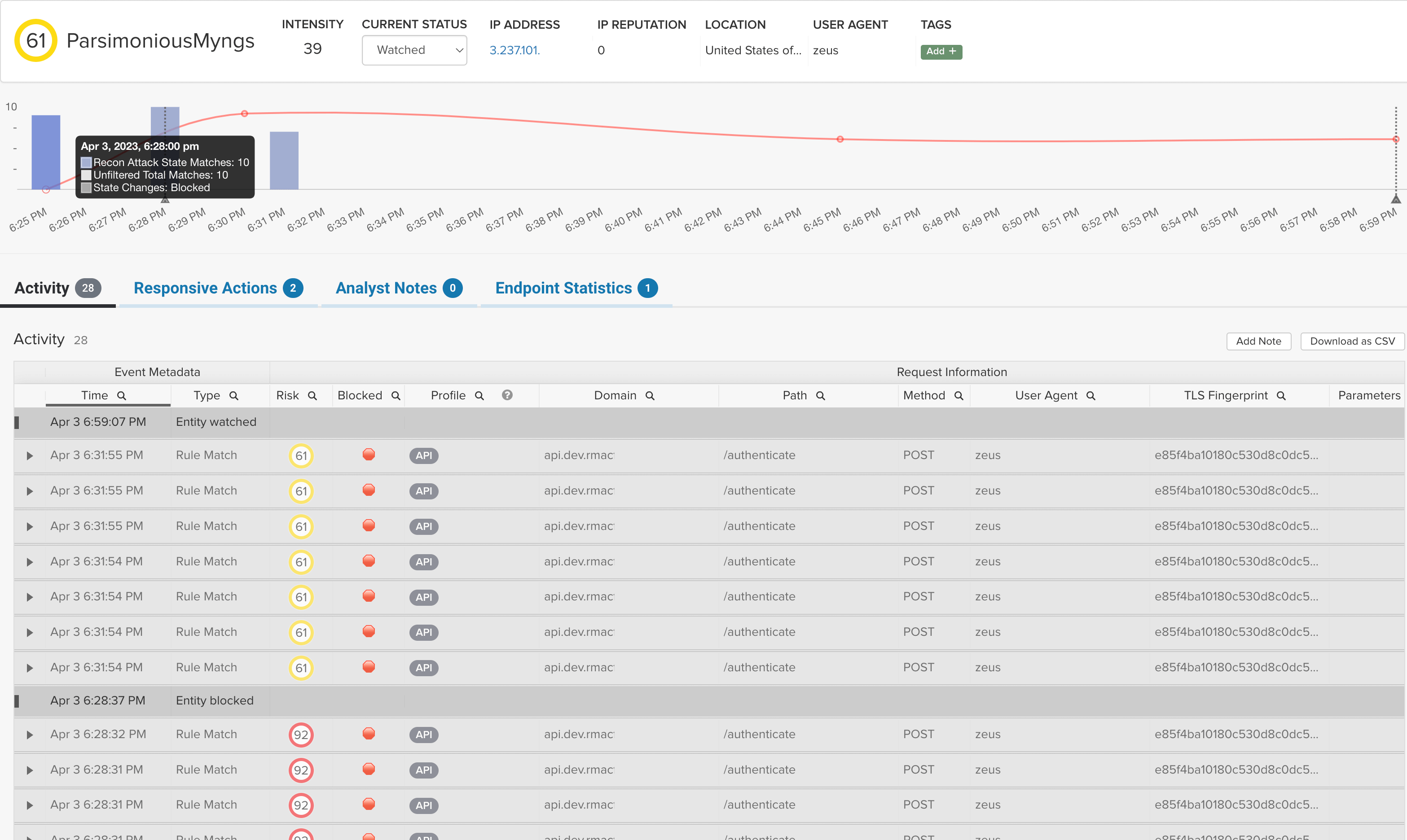
Threat Visibility
Understand what attacks you’re seeing without wading through complex dashboards
When it comes to threat protection, busy teams need to know their first line of defense gives deep visibility and defense against a variety of threats. ThreatX provides out of the box protection against many threats, including:
- OWASP Top 10 threats
- DDoS
- Malicious Bots and Botnets
- Credential Stuffing
We also automatically correlate evasive behavior like location masking and cycling IP addresses so you can quickly understand how threats are probing your disparate applications and APIs.
Stop Attacks in Minutes
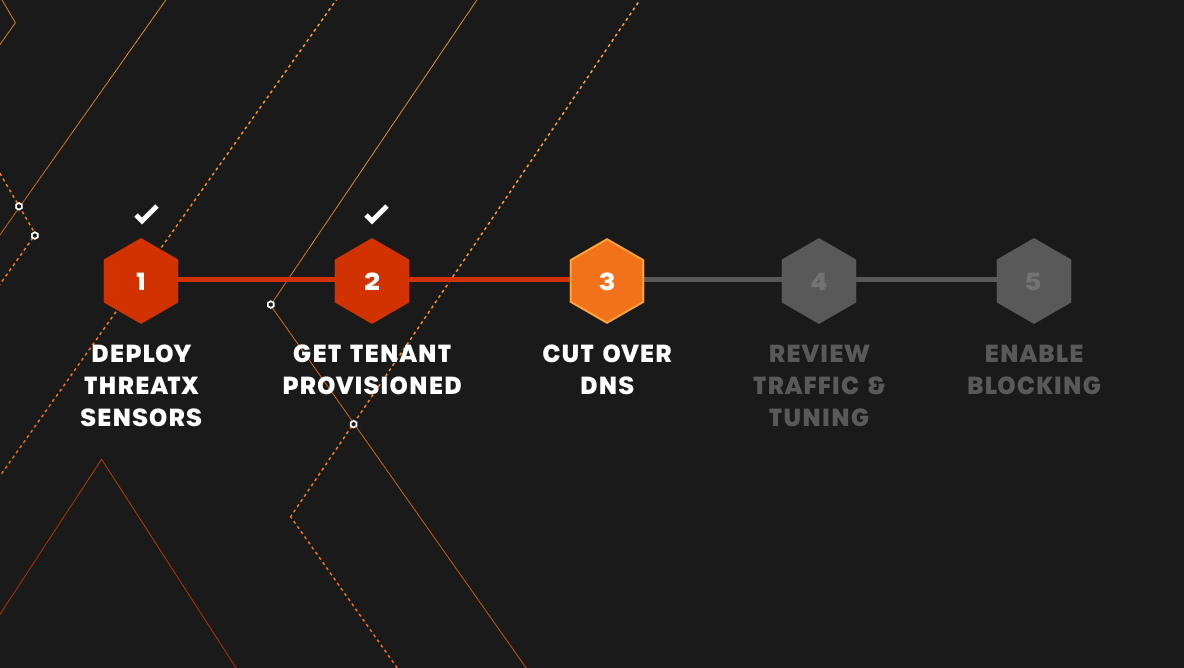
On board and protect new sites and APIs in minutes as opposed to days or weeks
New websites and APIs are constantly leveraged by organizations, and security teams need a solution that allows them to deploy protection quickly. With ThreatX, you’ll get instant threat visibility and protection for any application or API, deploying in minutes – not days or weeks. Your team will never need to waste cycles on granular configuration and time-consuming deployment efforts.
Frequently Asked Questions
Q1: How is ThreatX deployed?
A1: ThreatX is deployed as a reverse proxy and supports both SaaS and on-premises models.
Q2: Will I have to manage the ThreatX WAF?
A2: ThreatX is sold as a fully managed Protection-as-a-Service, and so all customers have access 24/7 to a team of experts who will help you with any issues you encounter using the ThreatX protection platform.
Q3: Can ThreatX protect multi-cloud environments?
A3: Yes. ThreatX is often chosen for its ease-of-use and flexibility protecting web applications and APIs no matter where they reside. We support all major cloud providers.