Looking for an alternative to Traceable API Security?
Secure all your APIs AND applications with observability, prevention, and protection.
- Visualize your application’s network and runtime traffic
- Discover all APIs and maintain documentation effortlessly
- Protect APIs (and apps) against botnets and threats
- Mitigate vulnerabilities faster with continuous detection, testing, & remediation workflows
Why ThreatX Prevent Might Be a Fit for Your Organization
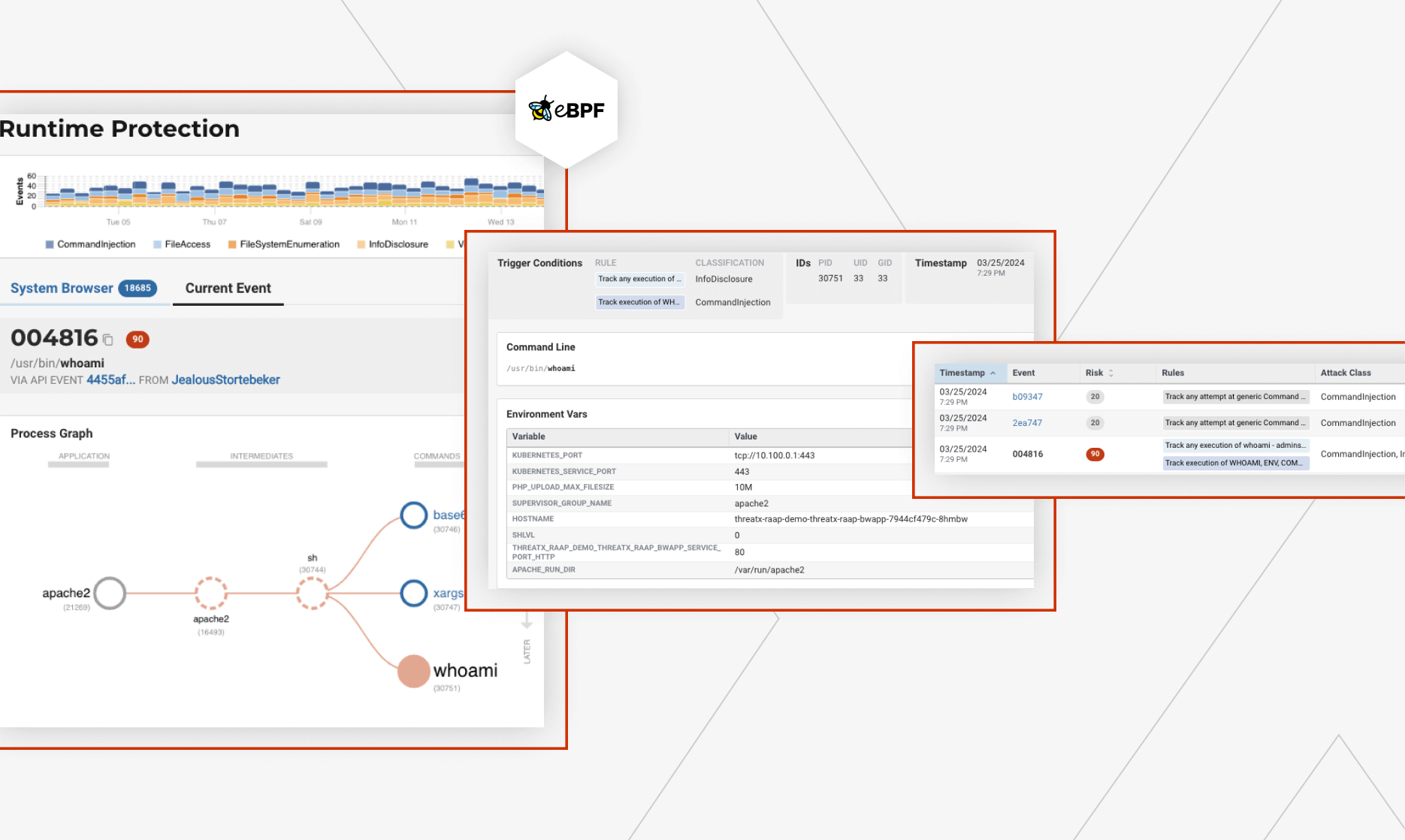
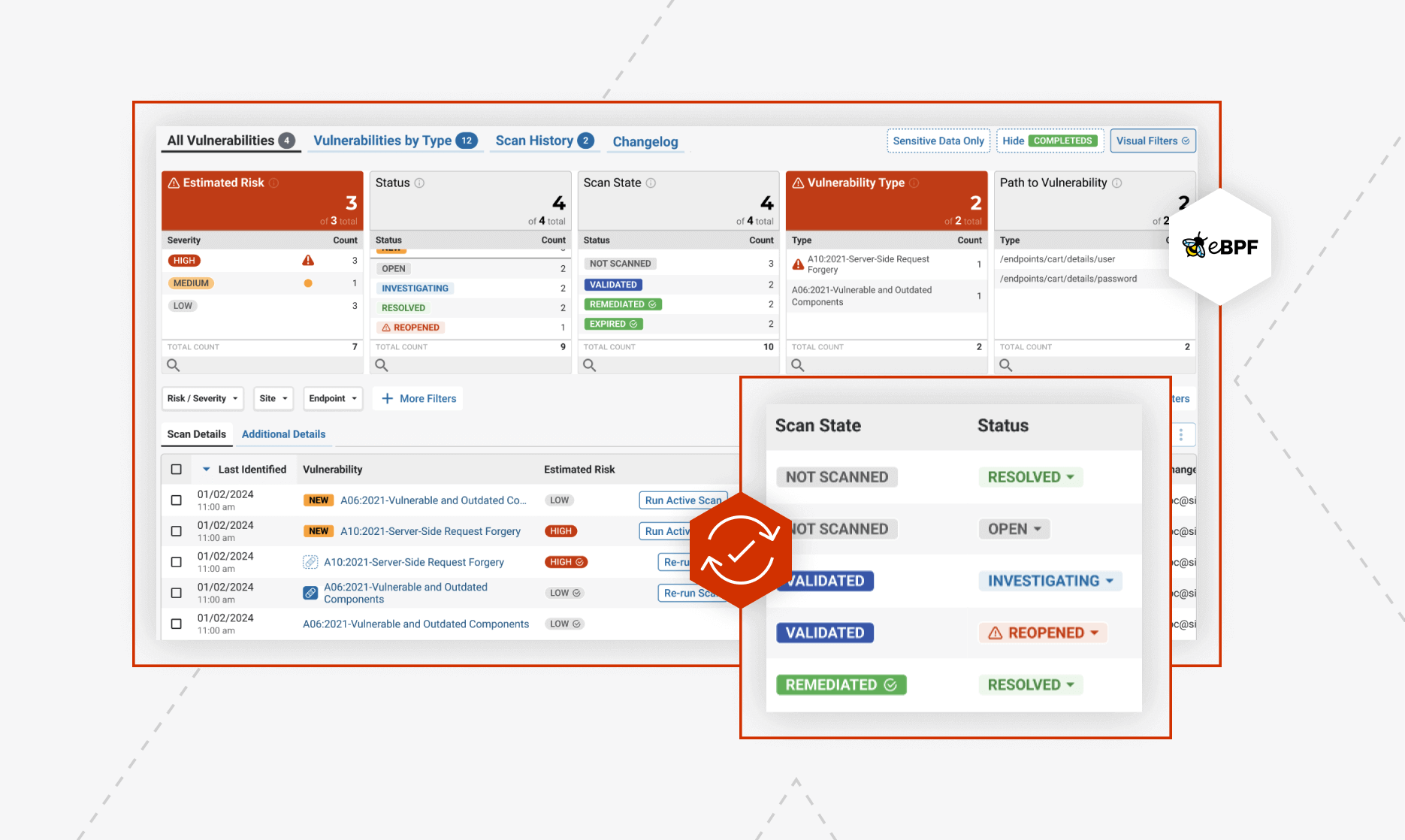
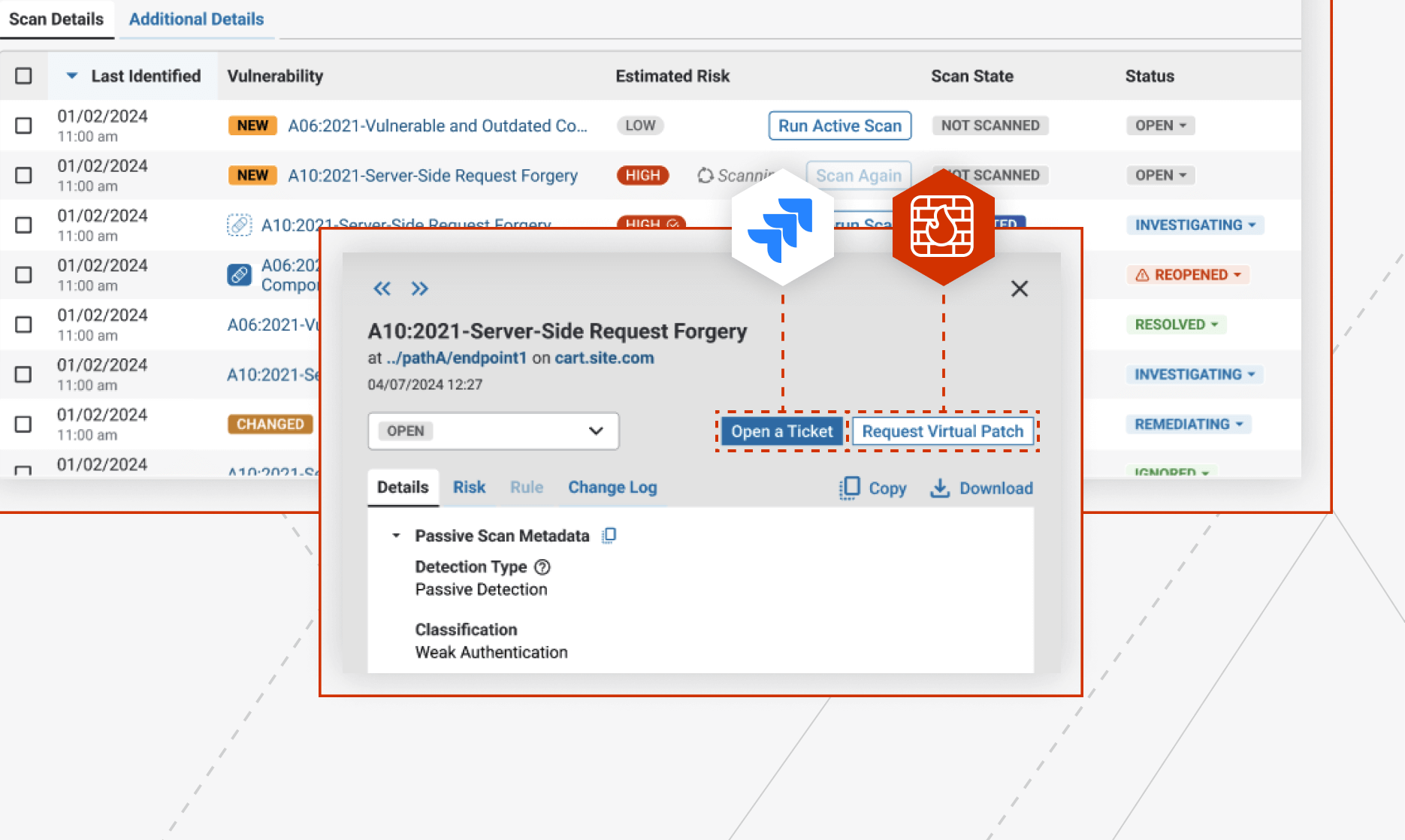
Prospects come to us frustrated that their dedicated API Security platform is creating too much noise to manage themselves. From keeping up with scanning cycles to an abundance of false-positive vulnerabilities muddying up development cycles, ThreatX offers a simpler and more consumable approach.
| Compare our Solutions | ThreatX Prevent | Traceable API Testing |
| Runtime Traffic Observability | ||
| Continuous Vulnerability Detection | ||
| Vulnerability Risk Assessment | ||
| Discovery for Internal & External APIs | ||
| API Specification Generation | ||
| API OWASP Top 10 Coverage | ||
| Native Dynamic API Testing | ||
| Software Composition Analysis | ||
| Vulnerability Prioritization Workflows with Ticket | ||
| Vulnerability Mitigation Workflows with Protection |
Why Prospects Choose ThreatX Prevent Over Traceable API Security Testing
Why ThreatX Protect Might Be a Fit for Your Organization
The top challenges we hear from prospects trying to protect their APIs & applications from threats starts from insufficient detection capabilities, struggles deploying in cloud infrastructure, and an abundance of false-positive alerts affecting user experience. ThreatX Protect offers a simpler and more effective approach.
| Compare our Solutions | ThreatX Protect | Traceable Attack Protection |
| Real-time HTTP Traffic Visibility | ||
| Behavioral Threat Detection | ||
| Native Web Application Firewall | ||
| Automated Threat Response | ||
| Protection for API Attacks | ||
| Protection for Web Application Attacks | ||
| DDoS Protection | ||
| Bot Mitigation | ||
| Discovery for External APIs | ||
| API Cataloging | ||
| Sensitive Data Exposure | ||
| API OWASP Top 10 | ||
| Fully Managed |
Why Prospects Choose ThreatX Protect Over Traceable Attack Protection
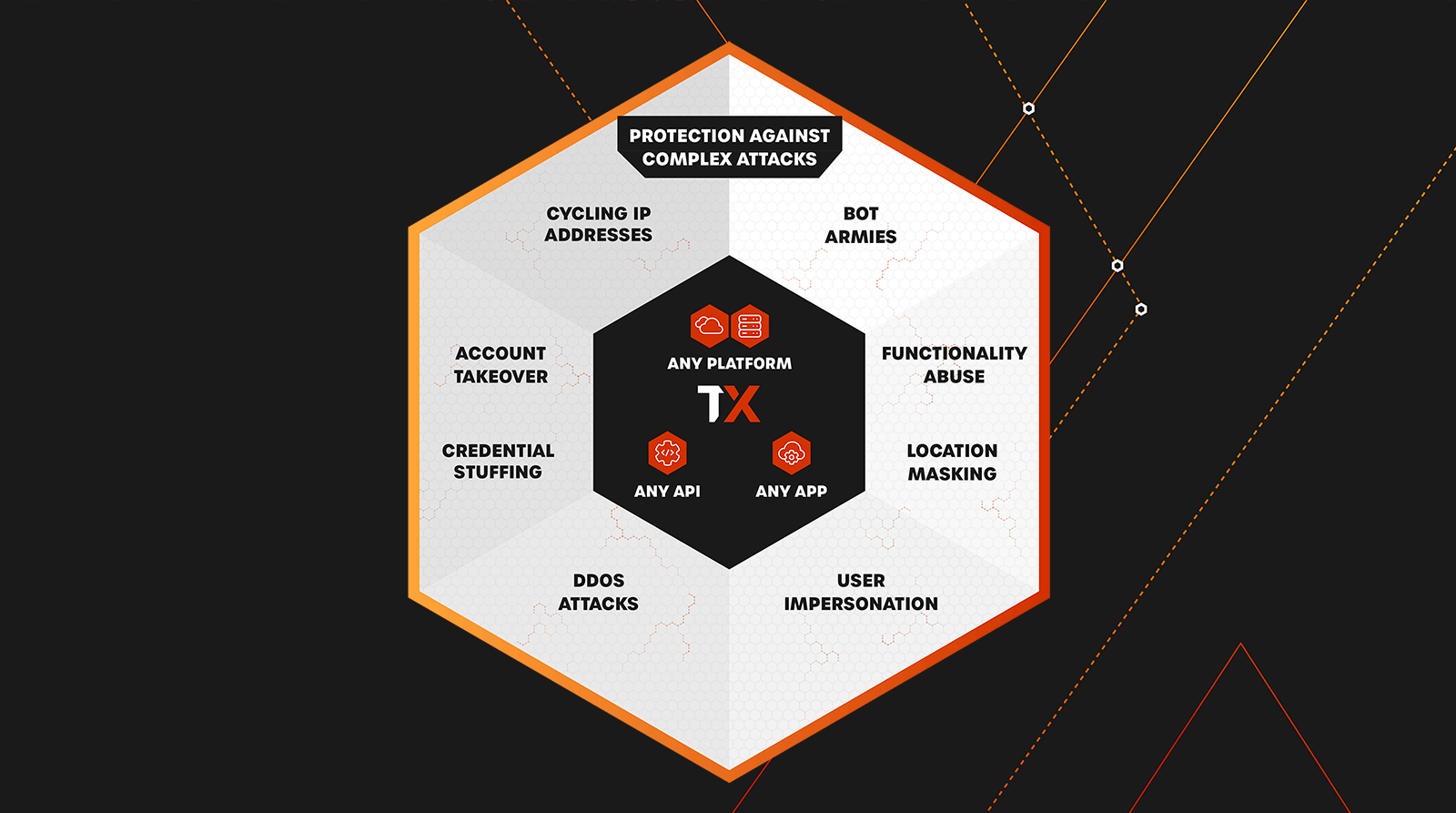


Protect Your APIs and Applications with Confidence, Not Complexity
ThreatX is managed API and application protection that lets you secure them with confidence, not complexity. It blocks botnets and advanced attacks in real time, letting enterprises keep attackers at bay without lifting a finger. Trusted by leaders like Lenovo, BMC and Epsilon, ThreatX profiles attackers and blocks advanced risks to protect APIs and web apps 24/7.