Looking for an alternative to Salt Security?
Secure all your APIs AND applications with observability, prevention, and protection.
- Visualize your application’s network and runtime traffic
- Discover all APIs and maintain documentation effortlessly
- Protect APIs (and apps) against botnets and threats
- Mitigate vulnerabilities faster with continuous detection, testing, & remediation workflows
Why ThreatX Prevent Might Be a Fit for Your Organization
Prospects come to us frustrated that their dedicated API Security platform is creating too much noise to manage themselves. From keeping up with scanning cycles to an abundance of false-positive vulnerabilities muddying up development cycles, ThreatX offers a simpler and more consumable approach.
| Compare our Solutions | ThreatX Prevent | Salt Posture Governance |
| Runtime Traffic Observability with eBPF | ||
| Continuous Vulnerability Detection | ||
| Vulnerability Risk Assessment | ||
| Discovery for Internal & External APIs | ||
| API Specification Generation | ||
| API OWASP Top 10 Coverage | ||
| Native Dynamic API Testing | ||
| Software Composition Analysis | ||
| Vulnerability Prioritization Workflows with Ticket | ||
| Vulnerability Mitigation Workflows with Protection |
Why Prospects Choose ThreatX Prevent Over Salt Posture Governance
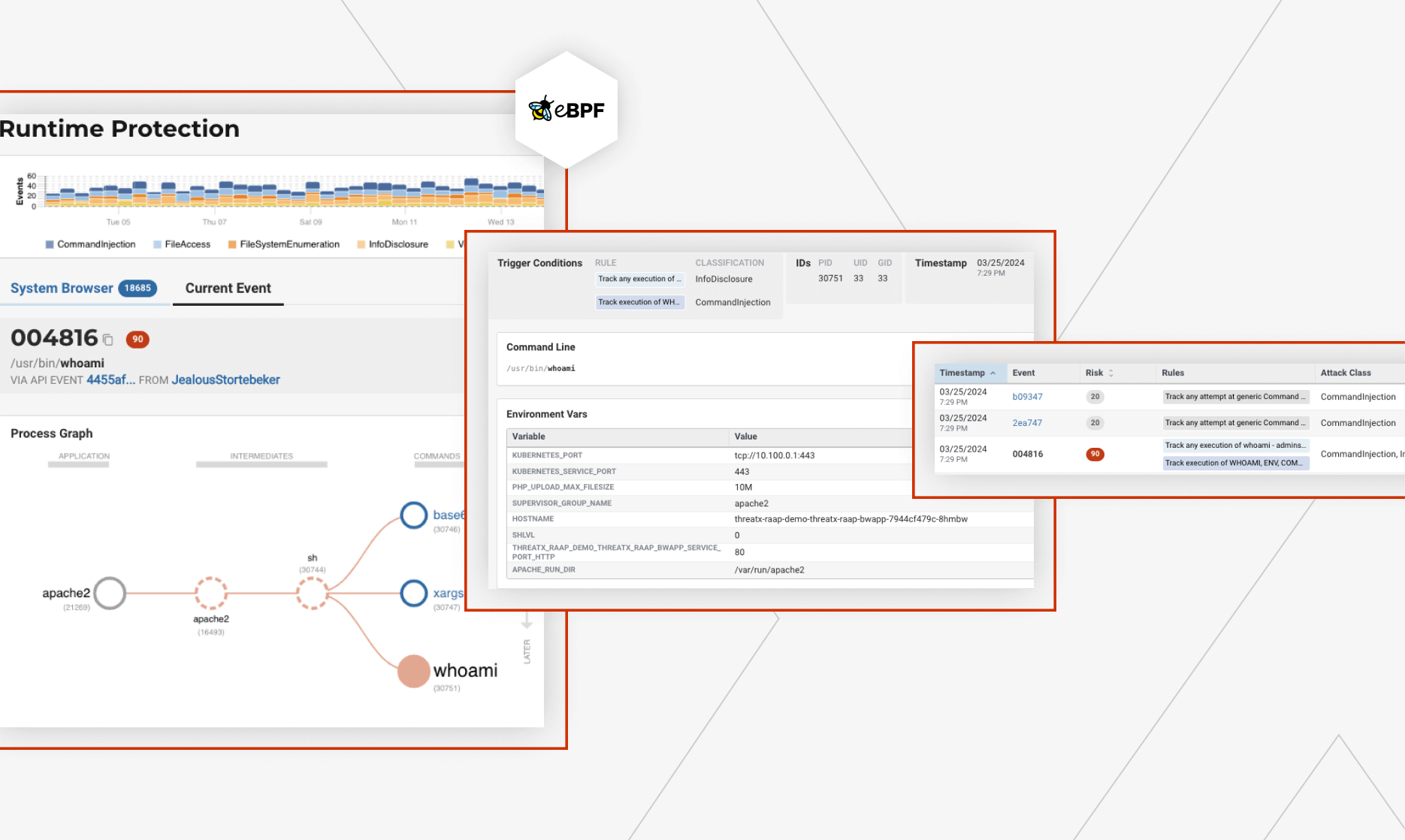
Runtime Observability for all APIs & Apps
Go beyond HTTP visibility with eBPF-powered runtime observability
Fueled by digital transformation, application development is moving faster than ever before. This rapid pace drives more vulnerable applications and APIs into production daily, leaving users’ data and organizations at risk.
Gain real-time observability into API/App runtime ecosystems, system calls, traffic data exchanges, threats, and vulnerabilities across containerized multi-cloud infrastructures with ThreatX Prevent.
Learn more about ThreatX’s runtime observability by listening into this webinar.
Continuous Vulnerability Detection & Native Testing
Equip your DevSecOps teams with continuous vulnerability insights
While most API testing solutions rely on traditional scanning, ThreatX Prevent leverages eBPF-based sensors for continuous vulnerability detection, allowing your team to identify high-risk vulnerabilities earlier. Additionally, its native DAST service delivers precise, targeted testing, enabling faster vulnerability confirmation than traditional time-consuming scans that probe an entire API.
ThreatX Prevent provides a unified approach to API Testing by combining continuous vulnerability detection and targeted dynamic tests. This equips your DevSecOps teams with contextualized vulnerability results, enabling faster prioritization and more effective remediation, fostering stronger collaboration across the board.
Experience ThreatX Prevent’s capabilities first hand by taking a product tour.
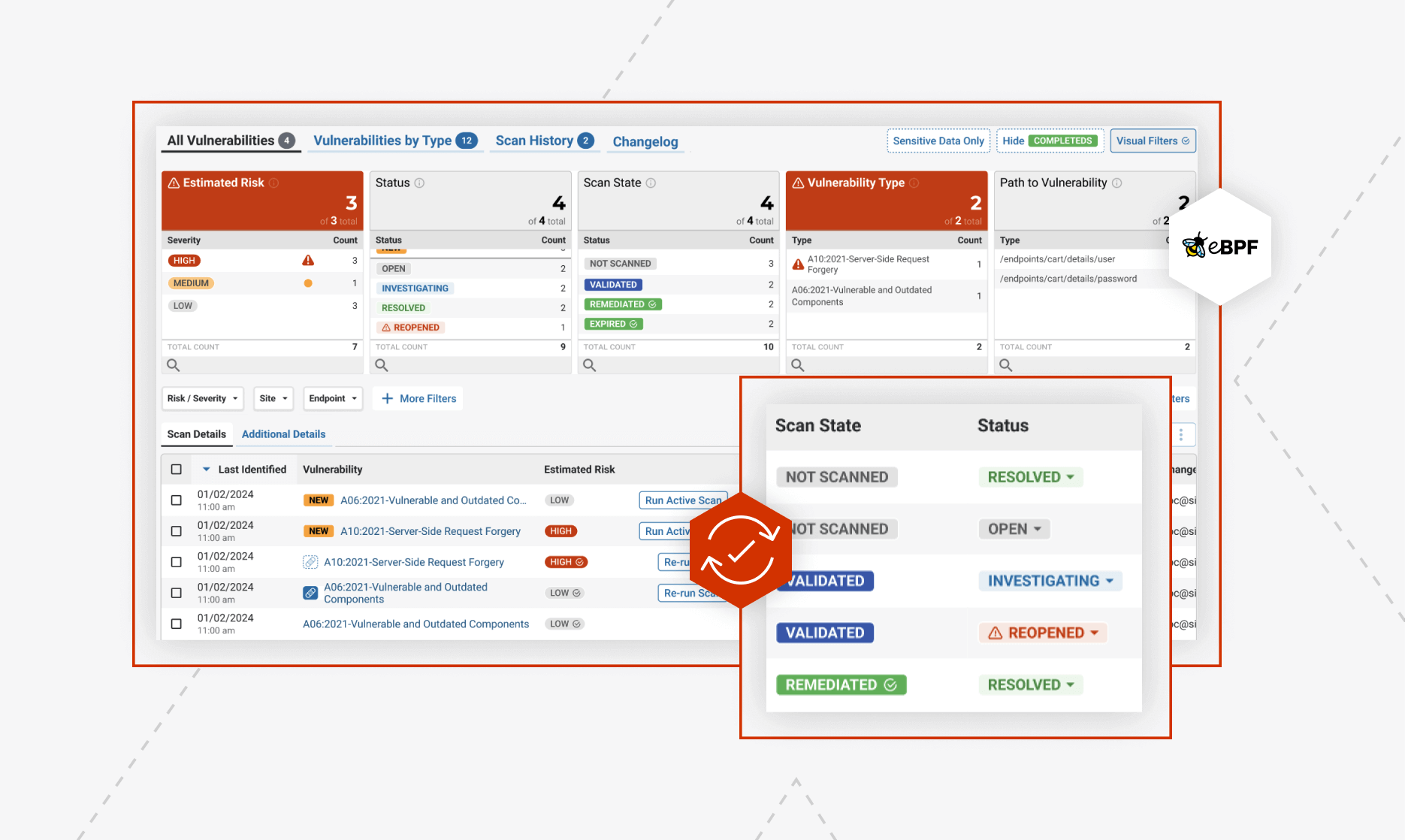
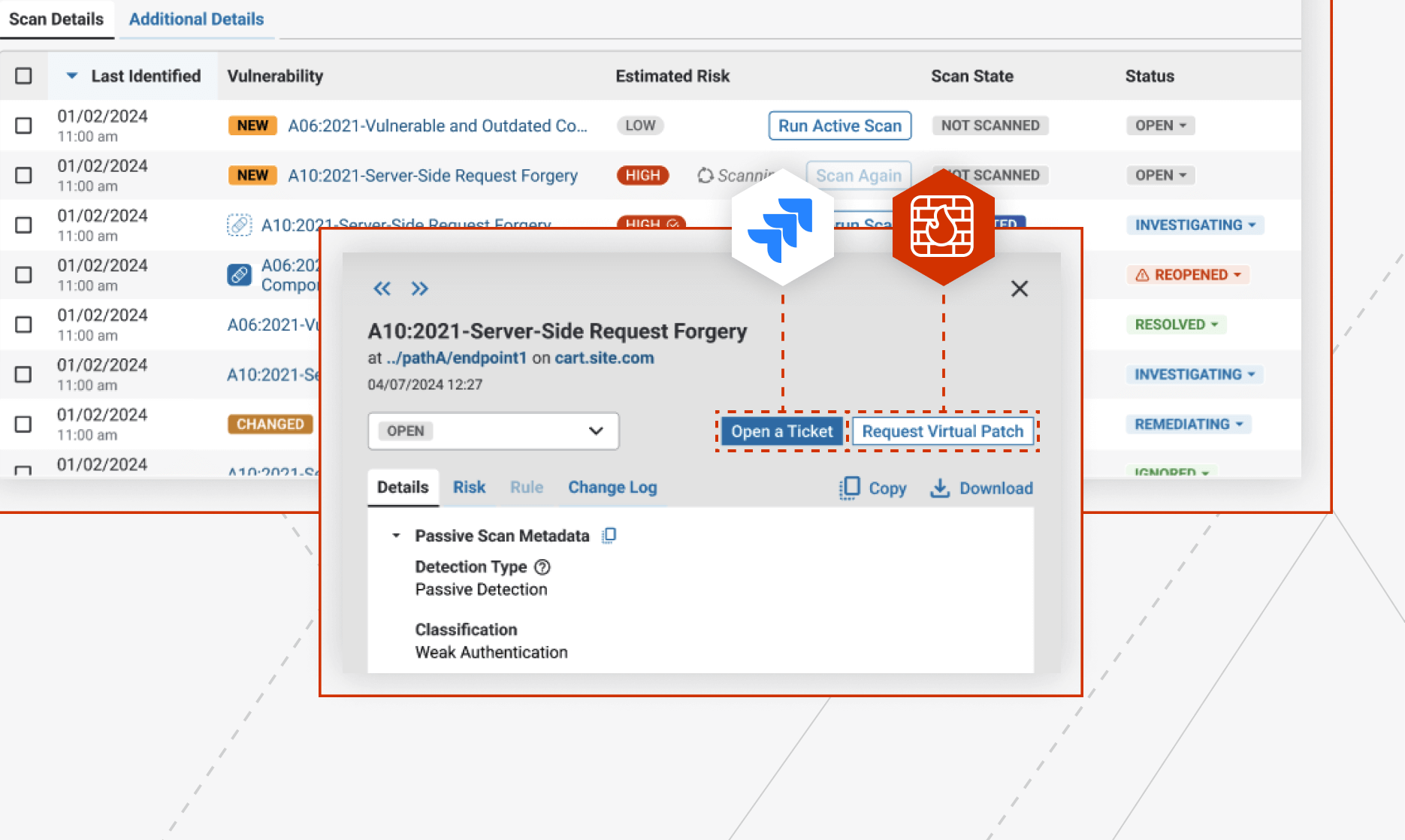
Risk-based Vulnerability Management Workflows
Drive remediation for risky vulnerabilities with ThreatX’s built-in workflows
In today’s fast-paced world, many DevSecOps teams struggle to manage and prioritize API vulnerabilities.
ThreatX’s Vulnerabilities Dashboard provides DevSecOps a holistic view of vulnerable APIs with workflows to address them including, virtual patching at the edge and integrations with development team’s ticketing systems. This approach ensures both development and security teams have one unified solution for preventing vulnerable APIs from being exploited.
Learn more about ThreatX’s vulnerability management workflows by reading this blog.
Why ThreatX Protect Might Be a Fit for Your Organization
The top challenges we hear from prospects trying to protect their APIs & applications from threats starts from insufficient detection capabilities, struggles deploying in cloud infrastructure, and an abundance of false-positive alerts affecting user experience. ThreatX Protect offers a simpler and more effective approach.
| Compare our Solutions | ThreatX Protect | Salt Threat Protection |
| Real-time HTTP Traffic Visibility | ||
| Behavioral Threat Detection | ||
| Native Web Application Firewall | ||
| Automated Threat Response | ||
| Protection for API Attacks | ||
| Protection for Web Application Attacks | ||
| DDoS Protection | ||
| Bot Mitigation | ||
| Discovery for External APIs | ||
| API Cataloging | ||
| Sensitive Data Exposure | ||
| Fully Managed Services |
Why Prospects Choose ThreatX Protect Over Salt Threat Protection
Protect APIs AND Applications
Protect more of your infrastructure from real-time attacks without managing multiple tools
Everything is increasingly complex.
From the infrastructure you’re defending to the attacks against it – security professionals need solutions that simplify.
With ThreatX, you can get deep threat protection for all your APIs and applications from a single platform. Not only can you protect both APIs and apps, but you can also discover, detect, track, and block with one powerful but simple platform.
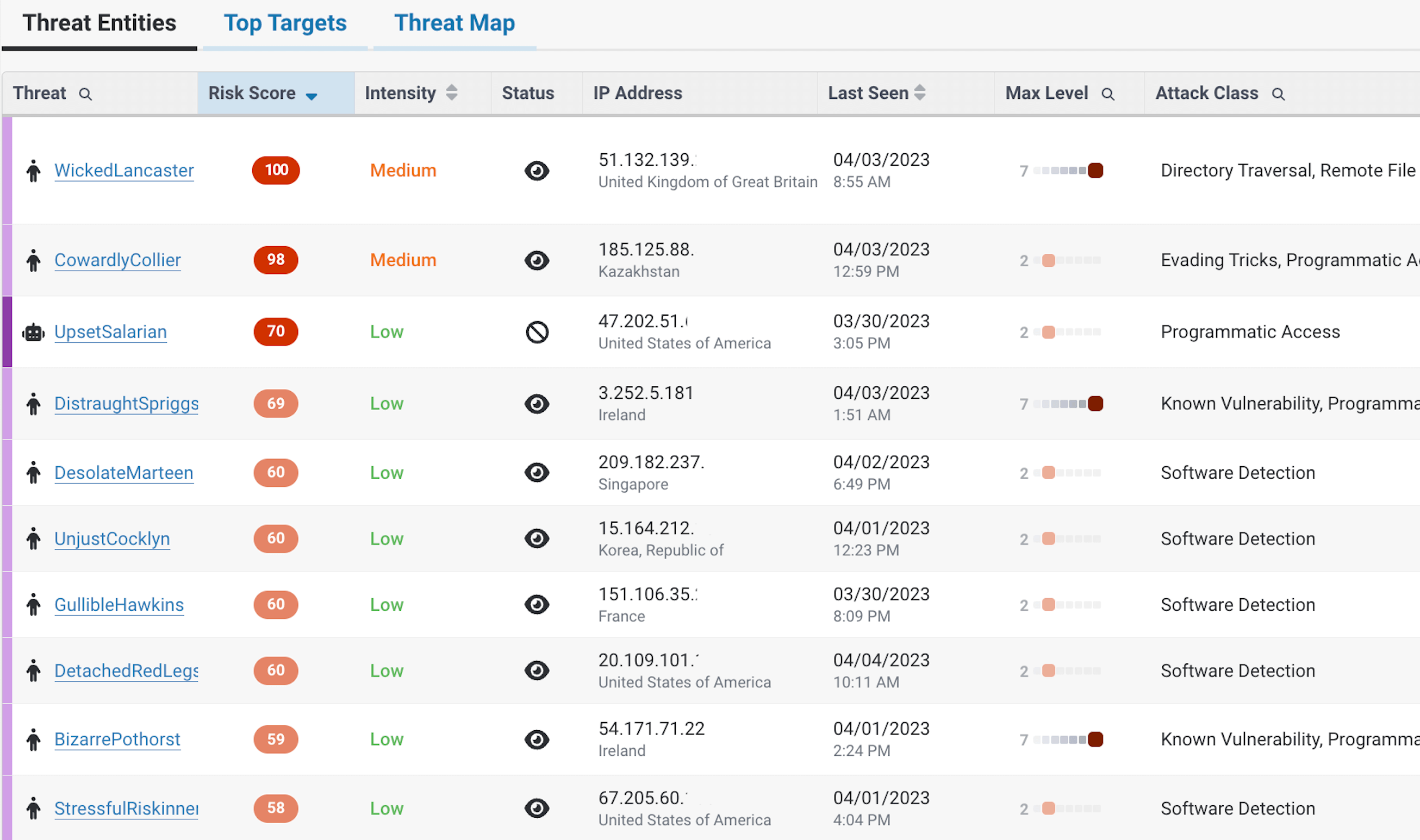
Native WAF & Automated Threat Protection
Block attacks in real time without integrating with a WAF or API gateway
Get the ability to detect, track, and block attackers all with a single solution.
There’s nothing more frustrating than the challenge of bolting solutions together only for latency or misconfiguration to miss real attacks. That’s why it was so important to architect a solution that could quickly protect, out-of-the-box protection against a wide range of threats.
With ThreatX Protect’s native WAF and automated threat protection, organizations can instantly block attacks based on risk, making false positives and alert fatigue a problem of the past.
Learn more about risk-based blocking with ThreatX.
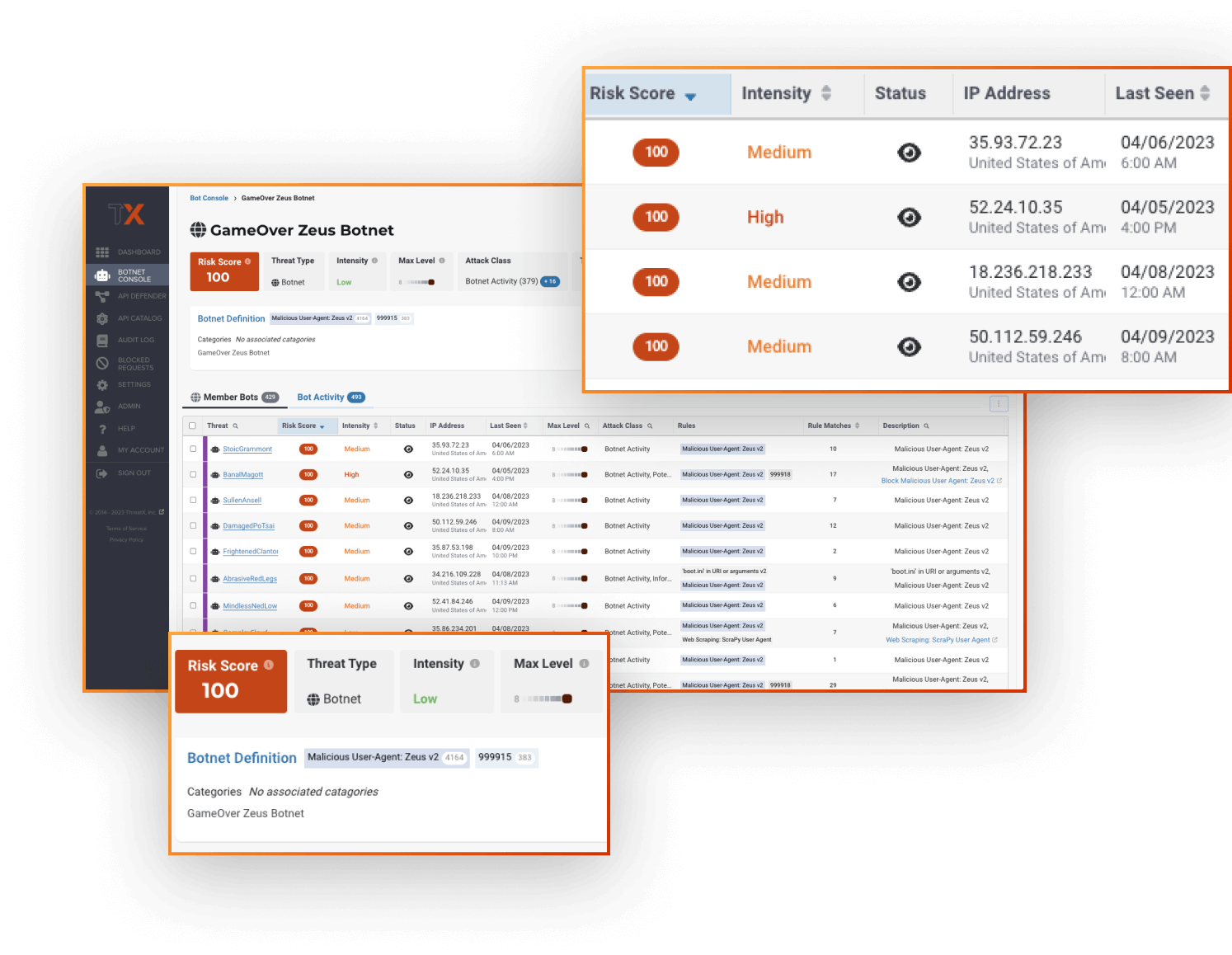
Advanced Bot & DDoS Protection
Monitor all bot & botnet activity, at scale – without wading through complex dashboards
Malicious bots interfere with a customer’s online experience, affect product availability, erode application performance, steal data, and even take over user
accounts. Stay ahead of advancing botnets & DDoS attacks with ThreatX’s advanced bot detection capabilities, utilizing a combination of techniques to identify a wide range of automated threats before they get a chance to advance.
ThreatX’s Botnet Console offers centralized analytics for streamlined tracking of bot activity within a single dashboard. This enables security teams to quickly identify the largest and most dangerous botnets driving malicious automated traffic. By diving into detailed traffic analytics, teams can monitor changes in bot behavior, pinpoint the noisiest bots, and spot those increasing in intensity.

Key Benefits
Secure APIs and applications with Observability, Prevention, and Protection
Eliminate risks without compromising your time or peace of mind.

Easy-to-Use
Experience user-friendly security designed to focus on what matters most. Leverage simplified dashboards so you can effortlessly oversee your API and application’s security posture and risks.
Easy-to-Manage
Get your nights and weekends back with always-active security that ensures your APIs and applications stay safe. Our visionary technology provides continuous protection and prevention without the need for manual intervention. Enjoy peace of mind knowing that your APIs and applications are secure even when you’re off the clock.
Eliminate Risks
ThreatX solutions are always monitoring, assessing, and identifying risks to APIs and applications continuously based on behavior. Our technology learns to recognize threats and vulnerabilities specific to your system, and proactively stops them based on risk level. This ensures your business remains operational and efficient, without interruptions.
Protect Your APIs and Applications with Confidence, Not Complexity
ThreatX is managed API and application protection that lets you secure them with confidence, not complexity. It blocks botnets and advanced attacks in real time, letting enterprises keep attackers at bay without lifting a finger. Trusted by leaders like Lenovo, BMC and Epsilon, ThreatX profiles attackers and blocks advanced risks to protect APIs and web apps 24/7.