Cloudflare vs Imperva
Looking for an Alternative?
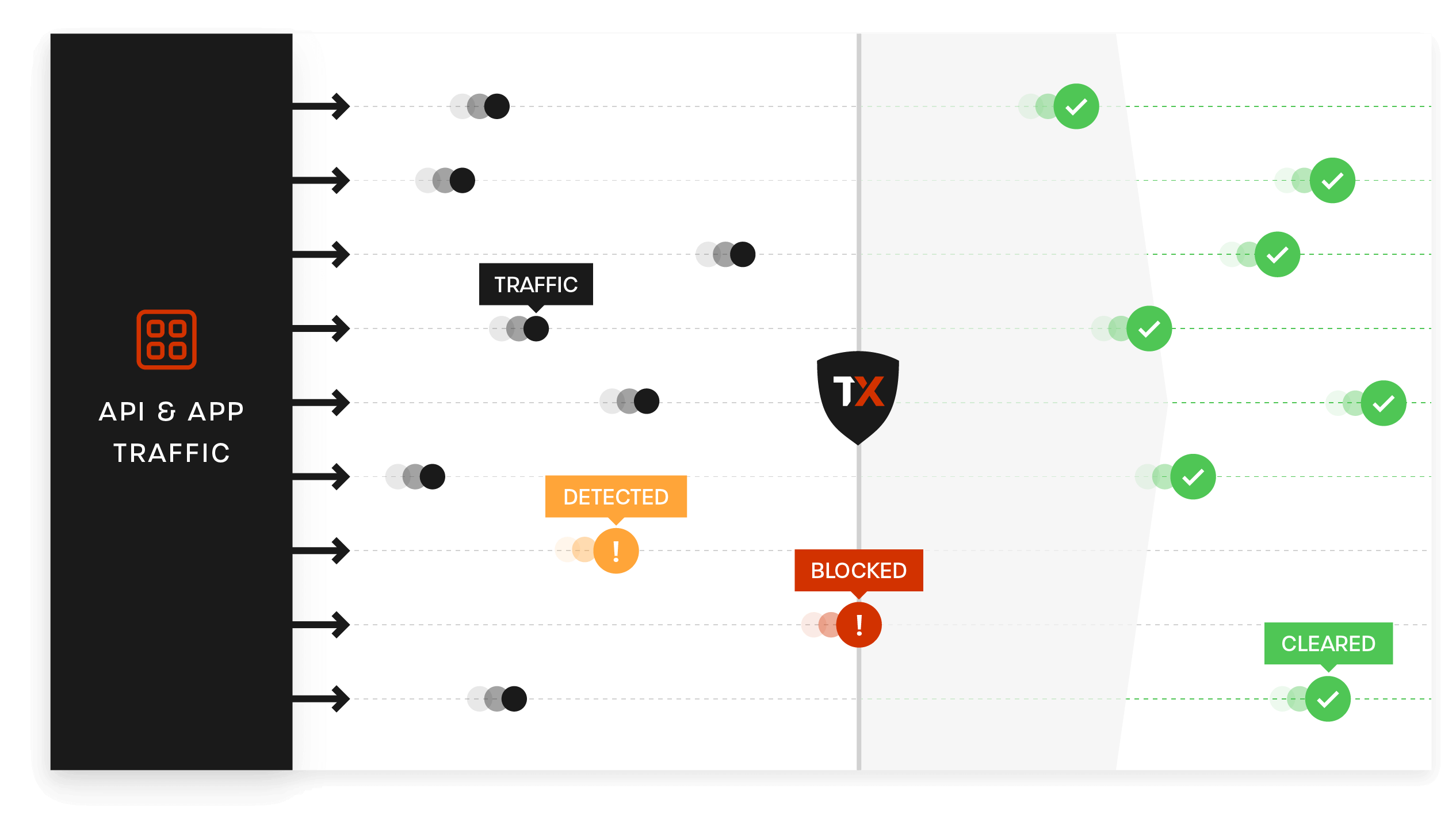
Secure your APIs and apps with observability, prevention, and protection – within one easy-to-use platform.
- Identify and stop attacks with risk-based, real-time blocking
- Get continuous API discovery, analytics, and threat investigation
- Protect APIs and apps against botnets, DDoS, and runtime attacks
- Ease burden on your team with a fully managed solution, plus 24/7 support backed by experts
- On-board and enable protection for multi-cloud environments in minutes
Why ThreatX Might Be a Fit for Your Organization
Prospects often come to us disappointed in legacy WAF solutions or frustrated that the dedicated API Security platform they just turned on is creating too much noise to manage themselves. From struggles deploying in cloud infrastructure to an abundance of false-positive alerts resulting in negative impacts to user experience, ThreatX offers a simpler and more practical approach.
ThreatX customers often value best-of-breed protection, simple management and deployment, along with the partnership they form with our Protection-as-a-Service team as an extension of theirs. Our platform is cloud-native and easily protects APIs and apps across any mix of cloud infrastructure.
| Compare our Solution Features | ThreatX | Cloudflare | Imperva |
| Behavioral Threat Detection | |||
| Risk-based Blocking | |||
| Web Application Firewall | |||
| API Protection | |||
| DDoS Protection | |||
| Bot Defense | |||
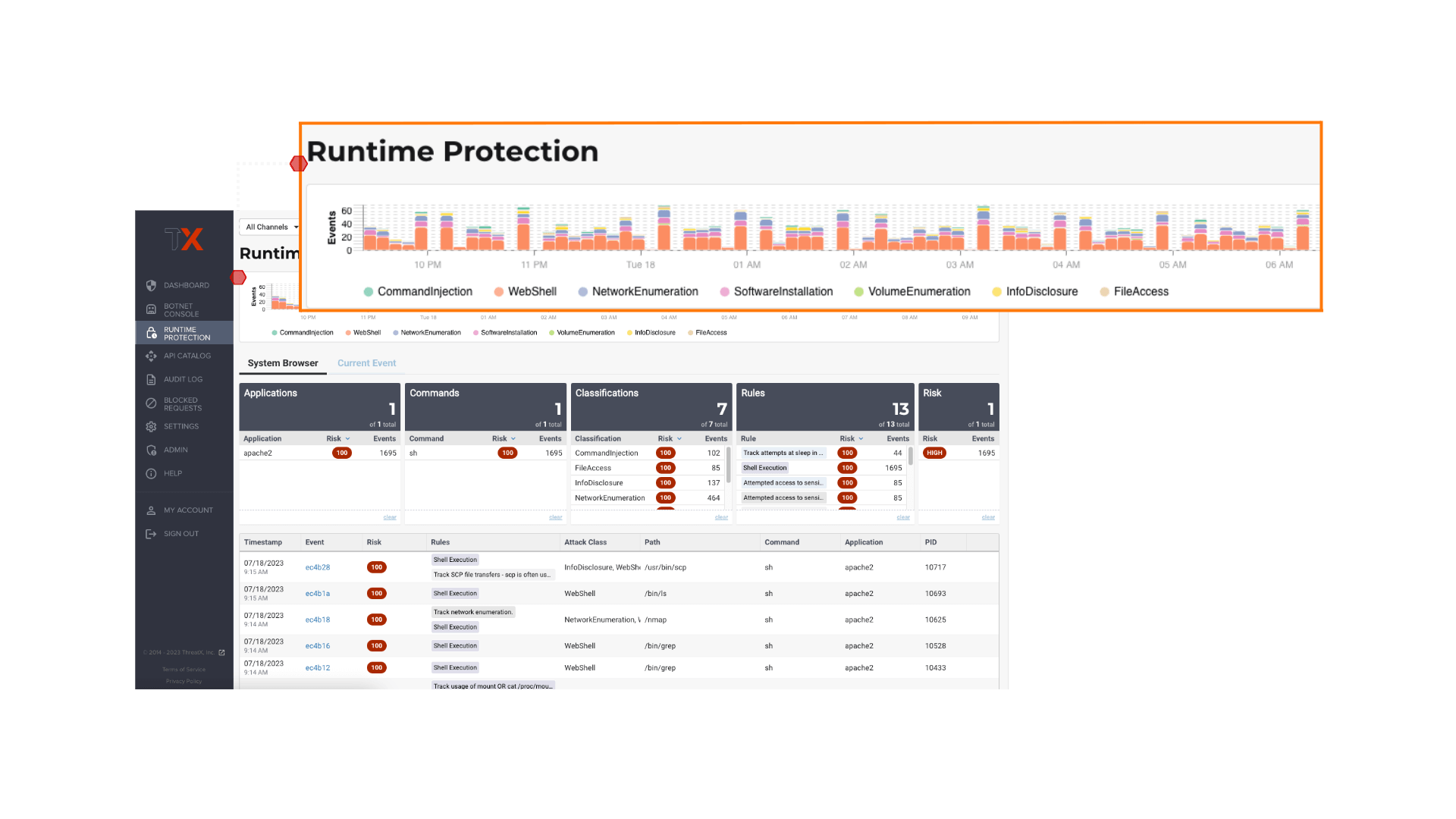
| Runtime Protection | |||
| Protection-as-a-Service | |||
| API Discovery | |||
| API Specification Generation | |||
| API OWASP Top 10 |
Why Prospects Choose ThreatX Over Cloudflare and Imperva


Protect Your APIs and Applications with Confidence, Not Complexity
ThreatX is managed API and application protection that lets you secure them with confidence, not complexity. It blocks botnets and advanced attacks in real time, letting enterprises keep attackers at bay without lifting a finger. Trusted by leaders like Lenovo, BMC and Epsilon, ThreatX profiles attackers and blocks advanced risks to protect APIs and web apps 24/7.