LAST UPDATED December 21, 2023
ThreatX offers both Runtime API and Application Protection (RAAP) and ThreatX API & Application Protection – Edge to provide a 360-degree ability to detect, track, and block threats to APIs and applications.
What is the difference?
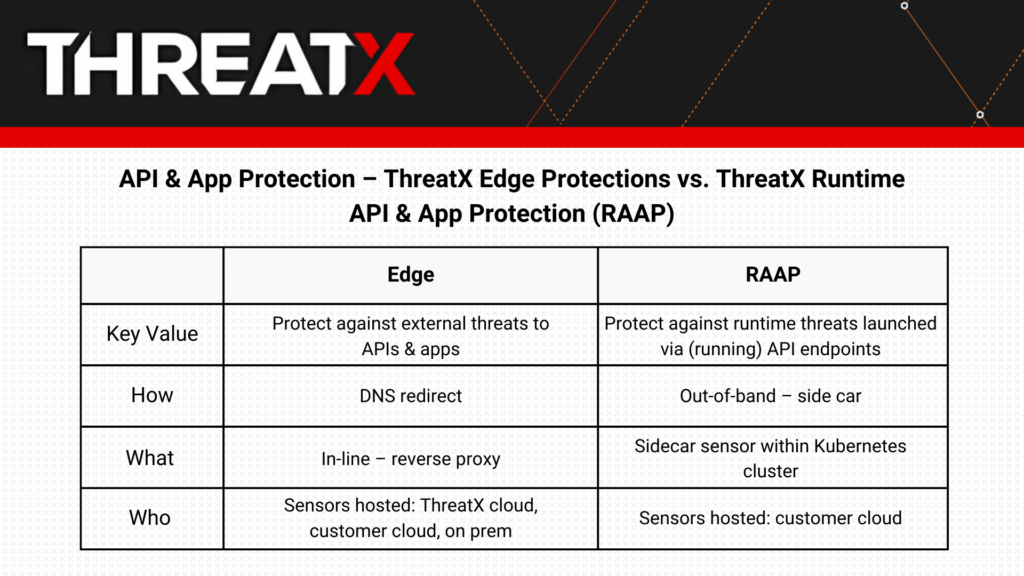
RAAP and Edge together provide comprehensive protection for APIs and applications. Edge monitors the traffic hitting your APIs and applications, identifying, alerting on, and, if needed, blocking threats before they gain access to your system. This protection is critical, but it doesn’t address threats that can arise from exploitations at the OS level, across in-network traffic (i.e., east-west), or zero-day threats. This is where our RAAP solution comes in, monitoring and protecting from the inside, at the operational side of your APIs and apps.
You can think of it as monitoring who is going into and out of a house, or also monitoring what’s going on inside a house.
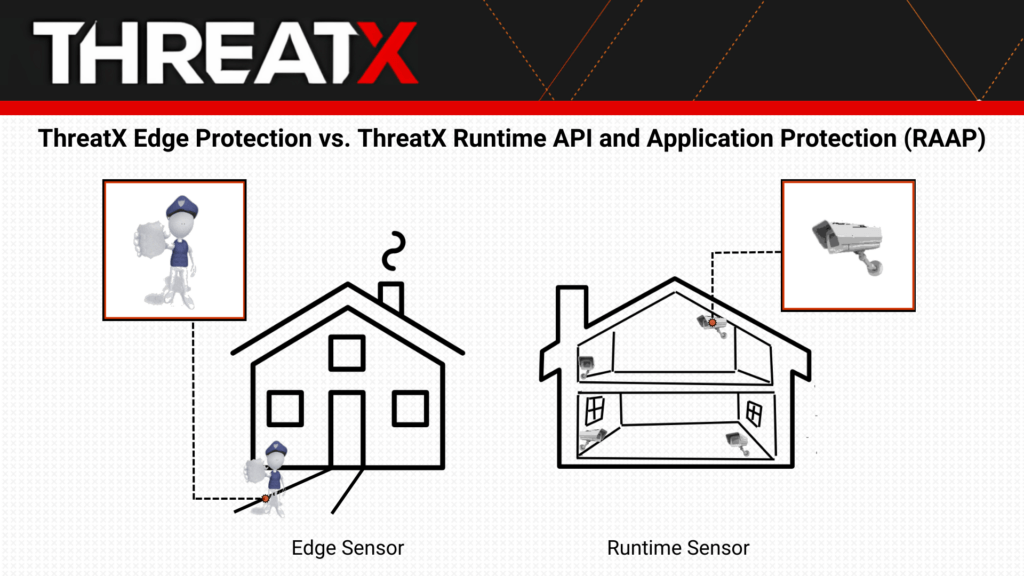
Our Edge sensor monitors HTTP traffic like a police officer monitoring people coming in and out of a house, keeping an extra close eye on anyone whose behavior seems suspicious, and stopping anyone who has raised a series of red flags, or who clearly has malicious intentions, from entering the house.
The RAAP sensor, on the other hand, is like also having cameras inside every room in the house that allow you to observe everything going on inside the house. These “cameras” would spot any intruders that made it by the police officer at the front door, and can take action if any suspicious or malicious behavior is observed.
With both the house and your API and application landscape – the two solutions complement each other and create a comprehensive security solution that allows you to see what’s coming in and out, and also what’s going on inside.
What types of threats does each address?
ThreatX RAAP and API & Application Protection – Edge together provide the most comprehensive protection because they each excel at identifying and blocking different types of threats.
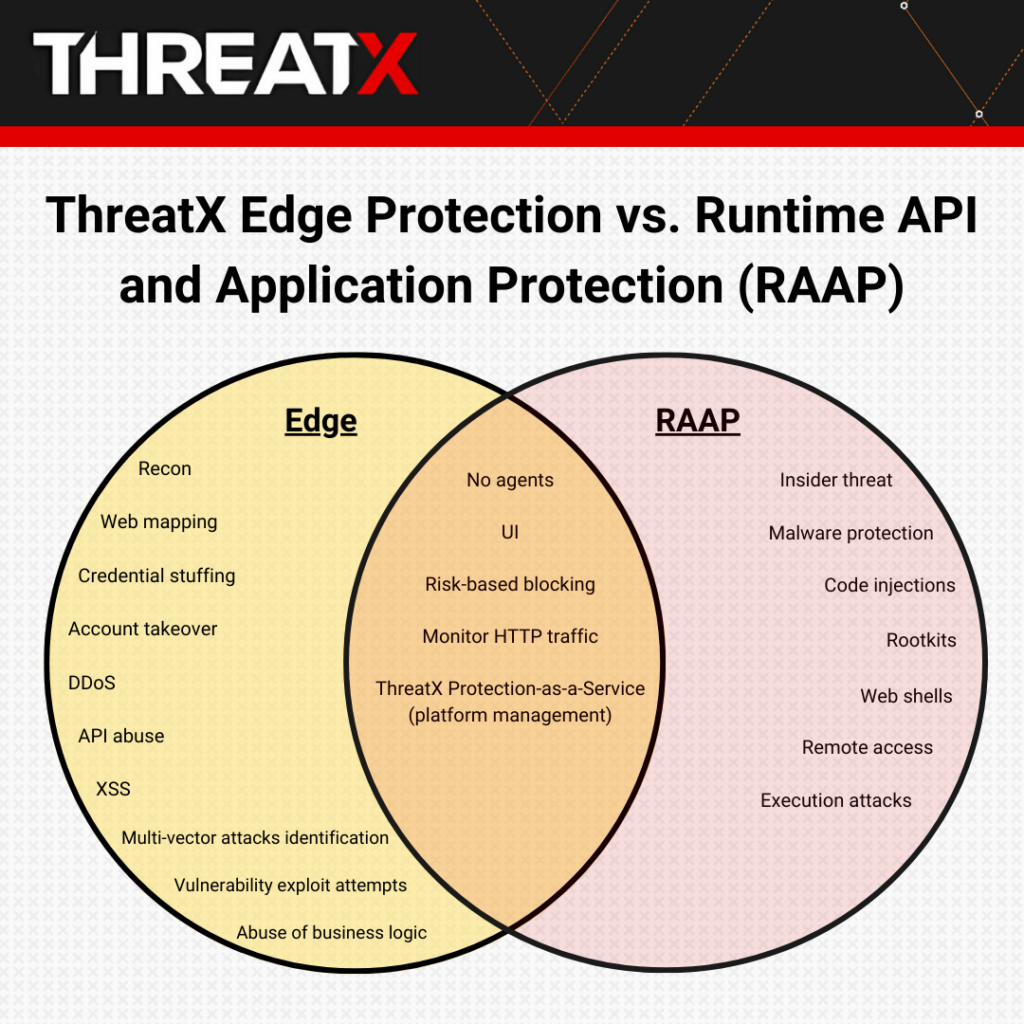
For example, Edge protection is ideal for identifying and blocking credential stuffing threats, and, in fact, ThreatX helps companies of all sizes in all industries effectively identify and block these types of attacks.
Back to the house analogy, if an attacker is flooding your APIs with credential stuffing attacks, ThreatX API & Application Protection – Edge would stop them before they even get in the “house.”
Read the story of a financial services organization that was struggling with credential stuffing attacks until partnering with ThreatX.
ThreatX Edge protection is so successful in defending against these types of attacks because it doesn’t just look for signatures of attacks, which is typically ineffective today with attackers who cycle through different IP addresses, attack techniques, and tactics. Instead, ThreatX Edge protection uses techniques including active interrogation, advance fingerprinting, attacker behavior analysis, and more to track attacker behavior over time and block when a certain risk threshold has been reached.
Learn more about credential stuffing and how we address it.
On the other hand, RAAP can identify threats that bypassed the front door and are now in the house — for instance, someone you trust but now has a nefarious intent (insider threat), someone who seemed harmless and was allowed in through the front door (a zero-day threat), or someone who enters through an unprotected side door (east-west traffic).
The ThreatX RAAP solution is deployed as a sidecar container within a Kubernetes environment. Leveraging extended Berkeley Packet Filter (eBPF) technology, ThreatX RAAP enables deep network flow and system call inspection, process context tracing, and advanced data collection, profiling, and analytics.
The RAAP sensor can identify rogue applications or processes running on your workload in the cloud. For instance, if an attacker exploited a vulnerable web application parameter, injected a harmful OS command, and the web server executed the injected command, RAAP would identify that execution.
Other examples of runtime API and application threats include malware, web shells, remote access software, insider threats, and malicious rootkits.
From the edge to runtime
The use of cloud infrastructure – and, often, multiple cloud providers – creates new sets of risk. Many attackers now prioritize finding backdoors – often by exploiting vulnerabilities in running applications – to circumvent edge and perimeter defenses. A comprehensive API and application security solution, with protection from the edge to runtime, is now required.
Learn more about runtime protection in our new whitepaper, Protecting Against Runtime Threats to APIs and Applications.
