LAST UPDATED March 18, 2022
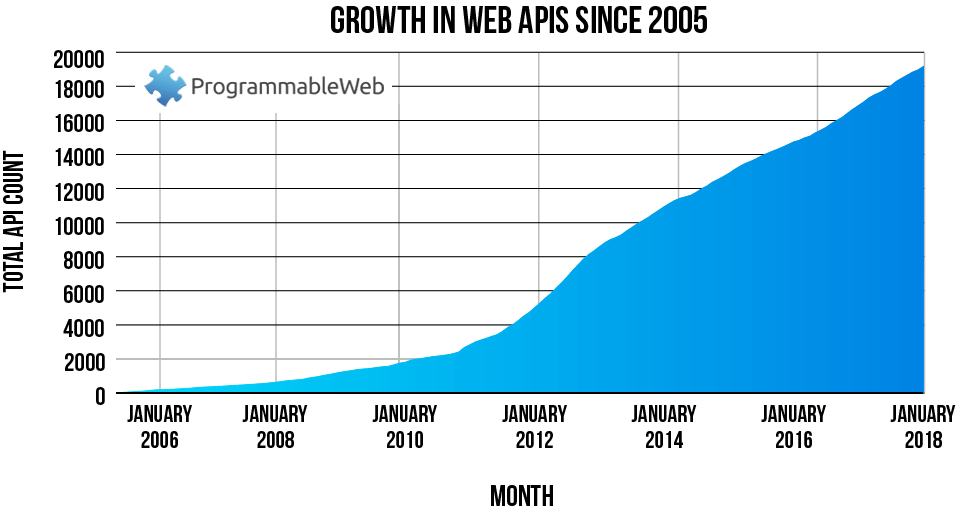
Application Programming Interfaces (APIs) are growing at an unprecedented rate. According to ProgrammableWeb, there were more than 20,600 APIs as of January 2019. That’s nearly a 230% increase in the last decade. And while APIs are better suited for today’s high-powered business model, they present a myriad of security challenges that must be addressed.
One of those challenges relates to access authorization in the Internet of Things. To simplify API implementation, developers will often use different methods, many of which introduce risks to the organization. The use of “long-term authorization tokens” is a perfect example. Instead of adopting industry best practices, which mandate the rotation of access tokens every few minutes, these tokens can be valid for days or even weeks. This provides an attacker the opportunity to hijack and reuse that token for days after it’s first issued.
 It is important to state, however, that even when transport encryption and authorization techniques are correctly implemented, there are still potential attack vectors. Often, these result from a lack of security protocols in the application design and come in the form of attacks, such as SQL Injection. And given that this is a fairly new occurrence, there aren’t many good options to mitigate these attacks – most Web Application Firewalls (WAFs) still don’t parse or examine JSON inputs.
It is important to state, however, that even when transport encryption and authorization techniques are correctly implemented, there are still potential attack vectors. Often, these result from a lack of security protocols in the application design and come in the form of attacks, such as SQL Injection. And given that this is a fairly new occurrence, there aren’t many good options to mitigate these attacks – most Web Application Firewalls (WAFs) still don’t parse or examine JSON inputs.
So what’s the solution? We’ve found the key to be designing, building, and connecting to your APIs from the start with security in mind. And there are five main points to consider when doing so:
- Strong authentication, ideally using asymmetric encryption and a private key stored securely on the device.
- Relatively short-lived tokens. Rotate them at least once every 30 minutes.
- TLS transport encryption.
- Standard authentication/authorization needs enforced for every endpoint. Avoid publishing unprotected endpoints.
- Sanitize user input, even if it’s coming from a device. A malicious user could manually manipulate requests to exploit faulty business logic.
With those five considerations in mind, you can eliminate many of the headaches that today’s security teams are facing. Implementing an API-compatible WAF can also go a long way in mitigating security issues and providing visibility into flows.
Learn more in the full article, originally published on IoT Agenda.