LAST UPDATED Mar 01, 2022
Whether it’s Auth APIs controlling access to privileged business logic in web applications, interservice communication connecting web apps to a data lake, mobile applications calling directly into a data center, or DevOps tooling connecting CI/CD pipelines to cloud-hosting providers, APIs are the common denominator!
Not surprisingly, the number of APIs in use is exploding. In fact, we at ThreatX have found that, among our customer base, for every one traditional website, there are, on average, more than 20 API endpoints. At the high end, we have customers with orders of magnitude more endpoints backing a single site. This rapid growth is not only rapidly expanding the attack surface, but it’s also making it more unknown and ambiguous. How? Well, that’s a story that makes for exciting reading: there are cowboys and zombies involved.
Yippee Kay Yay! How Rogue APIs Develop
All security operators know that “developers do stuff.” That’s their job. But even presuming positive intent, most enterprises are in the early stages of their API security program. Let’s say a developer needs to quickly stand up an API to resolve an immediate problem or develop a proof of concept. This API may be “cowboyed” into production outside official security and operational maintenance processes – no vulnerability scan, no consultation with security architects, no layer-7 protection. In short, no checks and balances. Now you have an API that is not in your API schema; it snuck into production, and now represents new and unintended attack surface. This creates what’s known as “rogue” APIs.
Moar Brains! How Zombie APIs Develop
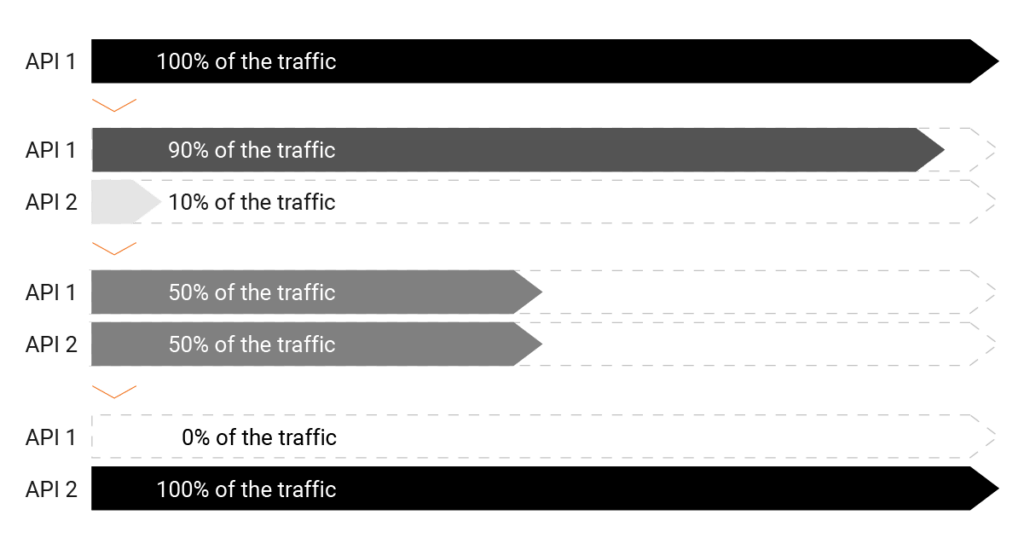
Then, there’s the living dead. Let’s say a development team is doing canary deployments. They create API Version 1, it’s valid and approved, and there’s a client calling API V1 over and over again. Then they create API Version 2 and start sending 1% of that traffic to API V2 instead, watch it, see if there are any problems, and if not, start sending more traffic to API V2, and less to API V1. Eventually, API V2 is getting all the traffic, but if you’re not careful, API V1 may still be out there. API V1 has now ended its useful life, but has not been deprecated, creating a “zombie” API – still out there creating risk. Maybe a vulnerability is discovered – and the team addresses it in API V2, but forgotten zombie API V1 is a fat, slow target for hackers. If you don’t know it’s out there, you don’t know you need to patch it.
You’ve got a lot of APIs. Rein in your cowboys, and double-tap your zombies. Protect all your APIs with one solution. Start here.
