LAST UPDATED August 27, 2021
We sat down with Andrew to learn more about his background and journey to CTO, what inspired the development of the ThreatX solution, get his perspective on the future of cybersecurity, and take a look at his new article series on TechTarget’s IoT Agenda Blog.
- What is your background?
From a security perspective, my background is a mixed bag. I have about 17 years of experience in various security fields, including consulting or working for large companies and startups. Throughout my tenure as a security professional, I have done my fair share of coding and developing, implementation of firewalls and IPS systems, compliance related work and, of course, web application firewalls.
- How did your background influence the development of the ThreatX solution?
In my work leading up to ThreatX, I experienced no shortage of issues with web application firewalls. The challenges ranged from selection to implementation and even maintenance. The legacy web application firewalls not only required the initial hardware purchase, but they also demanded either consulting hours or multiple FTEs to maintain signatures, handle the influx of alerts, and to simply manage the system. I grew increasingly frustrated and firmly believed there was a better way to deliver web application security. Unfortunately, at the time, there were no other options on the market and we were forced to utilize a system that was more of a burden to maintain than it actually provided value for us.
This experience grounded my focus and vision for the development of the ThreatX solution. My goal is to make web application security as simple and effective as possible.
- What makes ThreatX different?
We realized that one of the downfalls of legacy WAF solutions was the strong focus on individual attacks (or binary decisions). This approach, and the reliance on static signatures, is to blame for many of the fundamental challenges organizations experience with legacy WAFs, including high volume and cost of “false positives,” rigidity, and overburdened security teams.
Instead, our solution focuses more on the attacker to build a profile of different attack behaviors and specific attack vectors along the kill-chain. Our solution starts looking at and profiling an attacker as soon as they start conducting port scanning or reconnaissance.
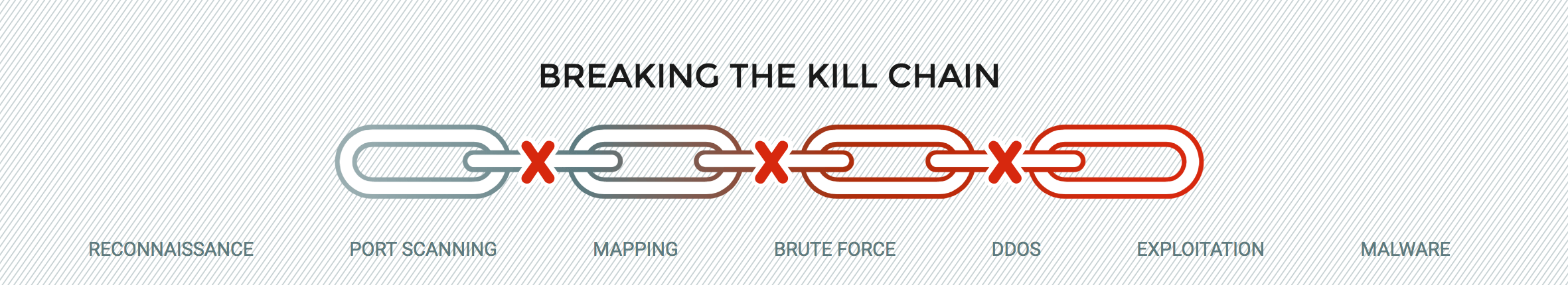
This allows us to track the behavior of each attacker and assign unique risk profiles. If the exhibited behaviors do not combine to reach a defined risk threshold, they are not blocked. Not only does this reduce the number of false positives, but it prevents legitimate traffic from being blocked prematurely. Once an entity exhibits truly malicious behavior, their risk score will increase and result in a block.
- Based on the analysis of ThreatX customer websites and applications, what are the most common vulnerability types organizations should keep on their radar?
Obviously, different organizations will have different application environments and threat profiles. They will also attract different hacker types. Regardless of these differences, however, the most common thing that comes across our radar is standard Internet noise, specifically in the form of Botnets trying to exploit WordPress sites. Cross-site scripts (XSS) and sequel injections are also very common.
One of our security engineers recently authored a blog series about detecting and protecting against bots.
- Why do reputation or signature-based WAFs fail?
Reputation feeds rely on flagging and blocking any and all potentially malicious IP addresses. The challenge with this approach lies with the growing sophistication of attackers. When the IP an attacker is using gets flagged, they will simply jump to a new IP – and they have multiple routes to do so – different shell accounts, Onion Routers, Open proxies, VPN providers, etc. So the list of malicious IPs only gets you so far.
Even if an organization has seen success with this approach, they will eventually end up with hundreds of thousands of IP addresses on a single blocking list. We have seen one Botnet use up to 350,000 different IPs. As a result, it is unrealistic to assume you can stay up-to-date utilizing this approach alone.
- What excites you about the future of cybersecurity?
Just look at the last decade in cybersecurity – The threat landscape is expanding and becoming increasingly challenging to protect. Hackers are getting smarter. Solutions are becoming more complex. And organizations are scrambling to keep up. It’s a completely different playing field.
Not to mention the proliferation of AI and machine learning. In the next few years, we may see AI engines “at war” with each other within the security space. I plan to take a front row seat to see how that plays out.
- Where do you see ThreatX in five years?
Simply put, ThreatX will continue to be a reliable WAF engine that fights off malicious hackers. That said, we will need to remain agile and iterative as the security landscape continues to change. We recognize that protecting organizations and their proprietary data goes beyond web applications and we fully intend on expanding our reach across the entire tech stack.
One of the first steps is moving beyond ingress flows and developing an egress sensor that will increase our visibility into things like phishing attacks and data exfiltration. We will also further integrate deeper machine learning and AI engines into our detection methods and into our sensors.
– – “The value of an idea lies in the using of it.” – Thomas Edison – –
- Where can we hear more about your perspective on cybersecurity?
In addition to my periodic contributions to the ThreatX blog, I am also a guest contributor for the IoT Agenda blog where I share insights on the challenges of managing and sufficiently securing all of the devices.
The future of ThreatX is reliant as much on the fluctuation of the cybersecurity industry as it is on the members of the team responding to those fluctuations. Andrew helps to define the culture here at ThreatX where each and every day is focused on improving the experience and effectiveness of web application security.
