In October 2022—three months before becoming a billionaire manchild’s plaything—Twitter suffered a high-profile cyber attack.
A hacker with the cliched, but nonetheless cool alias ‘devil’ posted that they had stolen the personal data of 5.4 million Twitter users.
Not only had the Prince of Darkness obtained the data, but they were also trying to sell it on a hacking forum.
You know, classic Lucifer hijinks.
This breach was possible because of a vulnerability in Twitter’s API, enabling the attackers to submit email addresses or phone numbers, and identify which account they were linked to.
Millions of people’s data were stolen, because of one vulnerability in one API.
Twitter also had to take on the financial cost of dealing with the incident and improving their security, and the reputational cost of the headline-grabbing breach.
I can’t imagine Lea Kissner, Twitter’s CISO at the time, got much sleep that month.
A breach like this is a CISO’s worst nightmare, and with good reason. It could force your entire company to grind to a halt, and have huge consequences both now and in the long run.
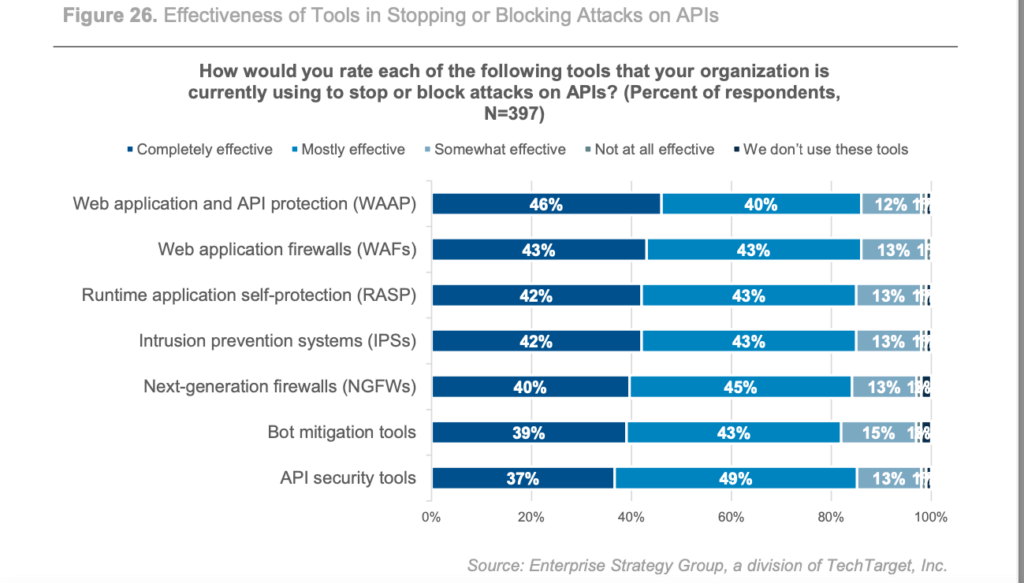
But that doesn’t mean you need to lose sleep worrying about API attacks.
In this article, we’re going to explain:
- What is an API attack, and what are the symptoms?
- Common signs you might be experiencing a breach
- How to protect your company from API attacks
By the end of this blog post, you’ll have a clear understanding of how API attacks happen, and what you and your company can do to give yourself the best chance of avoiding them.
Need help preventing and detecting API attacks? Book a live demo to see how attackers probe APIs, and how ThreatX stops them.
The cost of an API attack
Before we delve into the ramifications of an attack, and what you can do to prevent them, it’s important to define what we mean by an API attack.
In a nutshell, an API attack is a malicious attempt to exploit one or more APIs, with the goal of stealing sensitive data or disrupting the victim company’s services.
More often than not, this is done for financial gain. Which can be from acquiring credit card information, selling the stolen data, or blackmailing the breached company, among others.
And as the world relies more and more on data, these kinds of attacks are increasingly common. Especially on APIs, that are often direct lines to company data.
These attacks can cost your business in a number of ways.
Not least of which is the impact on your day-to-day operations.
When you’re a victim of an API attack, everything goes on hold until it’s fixed. Current projects, security initiatives, auditing, etc. Depending on the severity of the breach, an attack could halt your entire business operations.
And how long it takes to get back to business as usual depends on the depth and efficiency of your incident response process. Which isn’t a simple process, as you’ve got to:
- Detect and locate the breach
- Isolate and contain the threat
- Shut down the attack
- Find and communicate a workaround (which isn’t always possible)
While this is happening, you’ll have engineers working around the clock trying to fix the issue, crisis management, and pressure from customers and stakeholders.
Basically, no one is getting any sleep for a while!
For example, a client of ours was the victim of a bot attack on their APIs. The attackers targeted their sales CRM, where the client stored all of their client records, sales data, quotes, etc.
The attack brought the APIs down for ten consecutive days.
This sent their sales, new business, and client relations activities grinding to a sudden and costly halt.
On top of this huge interruption to key business functions, attacks like this could potentially cost your company thousands, if not millions of dollars in sales.
And that’s just the impact if you know you’ve been breached.
You don’t know what you don’t know
From our experience, companies often don’t even know they’ve been attacked!
When we’re onboarding new ThreatX customers, it’s not uncommon to notice anomalies in their APIs, dig deeper, and uncover unauthorized access.
Imagine someone having your company and your customers’ sensitive data, without you even knowing it’s happened. And think what they could do with that data.
(Actually, don’t imagine that. It’ll cause nightmares!)
Common symptoms of a breach
A big issue is that people aren’t aware of the common signs that indicate your APIs have been attacked, or are actively being attacked.
So let’s break it down, so you have a better idea of what to look for:
Slow API responses
If a script normally takes a couple of hours to run, but today it’s taken six hours, that means something is probably hitting your API pretty hard.
There are valid reasons for your API responses to be slower than normal, but it’s worth investigating if you notice this.
Unusual traffic patterns
Similarly, if you’re noticing unusual patterns in your request traffic, it could be a sign something sketchy is going on.
Keep an eye out for things like spikes in traffic, or lots of requests from the same IP address. Essentially, look out for any changes to the traffic you can’t explain.
Increased error rates
If you see an increase in error rates, especially failed login attempts (403 errors), this is often a sign of a brute-force attack.
This is because they will be firing lots of requests with different variants of credentials, which will be pretty obvious, as long as you’re looking for it.
Customer access complaints
It’s not just a case of monitoring the APIs themselves, though. If you’re seeing an upturn in customer complaints or support tickets about access, this could also be a red flag.
If attackers are hijacking accounts to access the APIs, this could noticeably impact the customers’ experience. Things like being knocked out, receiving emails about changed passwords, etc.
Another problem with detecting API breaches is that there’s not just one single type of API attack.
In fact, nonprofit foundation OWASP releases a laundry list of API threats every few years.
2023’s list includes such delights as broken authentication, server-side request forgery, and security misconfiguration.
Preventing API attacks
API security isn’t about focusing on just one or two things, it’s about taking a broad and proactive approach to protect your APIs.
You need to include safeguards in your APIs, and have a clear view of all activity.
Ideally, you want to stop attacks before they even get going. But as new threats emerge all the time, you also need to be able to identify an attack as soon as they start.
This means having granular control over who and what is accessing your APIs, and having the understanding to use these controls effectively.
You do this by having the right people using the right tools that have the right features.
API profiler & catalog
The first step in stopping and detecting API attacks is to achieve a high level of observability. You can achieve this by going through your APIs, and profiling:
- Event types
- Methods
- Endpoints
Or, more accurately, by using a tool that does this for you.
Once your APIs have been profiled, you can generate an API catalog, which is a centralized repository detailing and giving you access to all your APIs.
Once you’ve done this, you can then monitor and analyze the performance of your APIs from one place.
This makes it easier to identify performance improvements, reduce resource consumption, etc.
But more importantly, it can help you to guard against attacks by identifying vulnerabilities, monitoring for unusual activity, and gathering valuable diagnostic information.
Basically, it gives you the visibility and observability you need to identify threats and counter outside attacks.
Granular rate controls
Once you’ve got clear visibility, you also need to think about actively preventing and guarding against attacks.
Rate controls do this by regulating the rate of requests to your API using a variety of techniques.
For example, you could have headers specific to the API, the endpoint, or even the particular API call being made. So to protect yourselves, you can put in granular rate controls that block calls that don’t have the right header.
So instead of having to shut down the whole API to stop an attack, you can be clinical and just block the harmful requests.
This reduces the impact of an attack, so your business and customers can continue unaffected. This buys you time and gives you room to effectively diagnose, stop the threat, and plug any gaps.
Frustratingly, there are many different types of rate control, and often people call the same things by different names.
But the names don’t actually matter. The important thing is having flexible rate controls that can be configured and tweaked to suit your APIs and environments.
In ThreatX, we provide this out-of-the-box in the form of rules. These rules are very customizable, looking at a large number of factors, including timings.
For example, we have a rule that will assign risk if an entity received more than ten 404 responses within ten seconds.
These rules can be applied across the entire tenant, down to a site or groups, or even to a single endpoint.
Whatever tool you use, the end goal is to have full control over your rate controls, so you can build match criteria from different key signals.
Behavioral Analytics
Sometimes it’s not as simple as looking at one request at a time to identify potential threats.
More and more, attackers are taking a smarter approach, adopting a low and slow approach, and outsmarting rule-based detection.
They manage this because with this approach the requests don’t necessarily look suspicious in isolation. And you won’t know what’s going on unless you take a step back, and look at the whole picture.
To do this, you need to analyze behaviors over a long period of time to spot risks and threats.
Think of it like you work in a hardware store.
There’s nothing inherently suspicious about someone walking in and buying a flashlight.
But if they’ve also bought plastic sheeting, several bottles of bleach, and a shovel this week, you might want to watch your back!
For your APIs, attacker-centric behavioral analytics solves this by looking at the whole picture.
It connects the attacker’s behavior across different attack vectors, looking at the individual requests, and linking them together.
This builds a profile of the attacker, so you can identify suspicious behavior. More specifically you’re looking for two things:
- Indicators of compromise
- Indicators of attack
Then you can use this information to fix the gap in your security and deal with the immediate danger.
Essentially, it means you can stop The Shoveller before they start shoveling.
In Closing
As we’ve talked about, API attacks can be devastating for a company, but there’s plenty you can do to protect yourself.
Once you have a clear view of the activity on your API, you can quickly identify issues, prioritize your resources, and make fast data-driven decisions.
And by putting tight and customizable controls in place, you can restrict traffic to your API at a granular level.
These measures, combined with behavioral analysis, give you visibility over everything that’s going on, so you can proactively stop attacks before they even get started
But most importantly, it means you can sleep soundly, knowing you’re unlikely to wake up as front page news.
Need help preventing and detecting API attacks? Book a live demo to see how attackers probe APIs, and how ThreatX stops them.
