LAST UPDATED April 2, 2024
We recently analyzed data collected on the ThreatX API and Application Protection platform from August through October 2023. Two stand-out trends we see across industries are 1) the prevalence of bot attacks, which are rampant across companies of every size and in every industry, and 2) the popularity of credential stuffing attacks. We also found that, not surprisingly, the banking industry sees the most attention from attackers – and specifically with authentication attacks.
Below we share details of and analyze ThreatX platform data from Q3 2023.
Most Common API and Application Attack Types
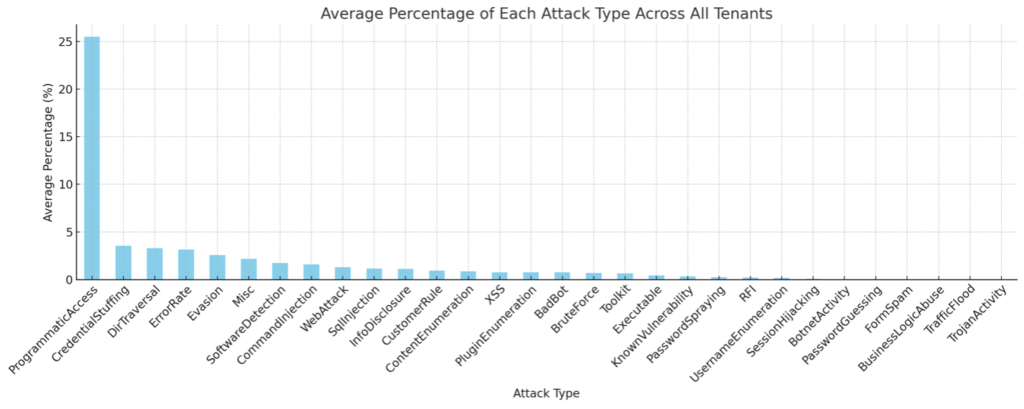
Figure 1: API and application attack types
Figure 1 highlights the top five most common attacks observed across industries:
- Programmatic Access: 25.49%
- Credential Stuffing: 3.53%
- Directory Traversal: 3.29%
- Error Rate: 3.16%
- Evasion: 2.58%
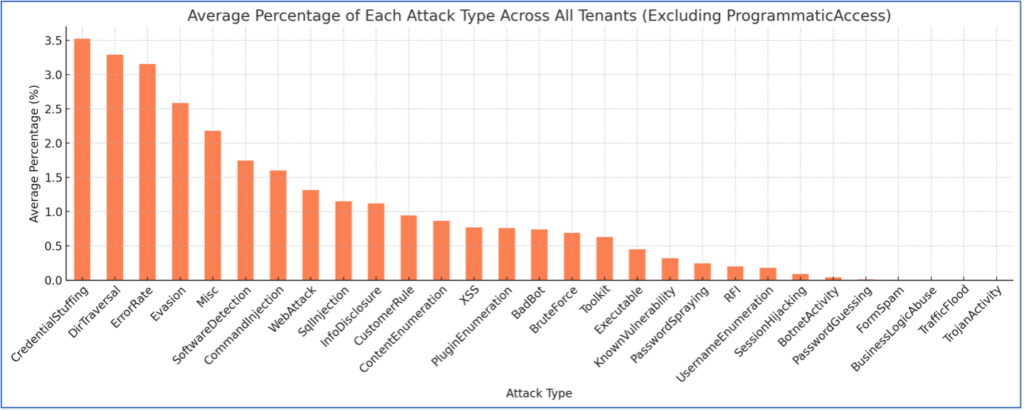
Figure 2: Attack types excluding programmatic access
After excluding programmatic access, the top five most common attacks are shown in Figure 2:
- Credential Stuffing: 3.53%
- Directory Traversal: 3.29%
- Error Rate: 3.16%
- Evasion: 2.58%
- Misc: 2.18%
Key takeaway
Programmatic access involves a wide variety of automated or non-human interactions with APIs and web applications, potentially aiming to scrape data, perform unauthorized transactions, or exploit vulnerabilities. The huge number of programmatic access attacks makes it clear that attackers are increasingly leveraging bots to look for weaknesses in organizations’ systems. Organizations should consider solutions that can track user behavior over time to better identify malicious vs. legitimate traffic. In addition, advanced threat engagement techniques, such as IP fingerprinting, interrogation, and tarpitting, help shed light on the “user’s” intent.
Definitions:
IP interrogation and fingerprinting: The ability to transparently present challenges and data-gathering techniques to determine human versus non-human users and create an identification profile used to track user activity across multiple IP addresses. This could be observing how the entity responds to automated challenges such as how the entity handles javascript or other types of code.
Tarpitting/rate limiting: The ability to artificially add delayed responses to a specific user suspected of malicious intent (DD0S, data leakage exploitation, etc.)
Programmatic Access: This type of attack involves automated or non-human interactions with web applications and APIs, potentially aiming to scrape data, perform unauthorized transactions, or exploit vulnerabilities.
Credential Stuffing: In a credential stuffing attack, attackers attempt to reuse credentials that were compromised in a previous breach in order to log in to another website or application.
Directory Traversal: Directory traversal is a type of exploit used by attackers to gain unauthorized access to restricted directories and files.
Error Rate: An abnormally high rate of errors in HTTP requests, often a red flag for either malfunctioning applications or malicious activity such as probing for vulnerabilities.
Evasion: Attackers frequently now use a variety of techniques to try to evade security solutions. If we see activity like varying timing of requests, randomizing header values, IP rotation, and encoding, we start tracking.
Attack Types by Industry
We break down the data by industry below, but at a high level, the main insights include:
High stakes in banking: The banking sector not only has the highest attack ratio, but also experiences a significant percentage of attacks against authentication (nearly 25 percent). This underscores the high stakes involved in protecting financial data and the attractiveness of financial institutions to attackers.
The multi-faceted nature of attacks in professional services: While this sector doesn’t top the list in terms of attack ratios, it does stand out in its variety of attacks. It has a relatively high percentage of bot attacks (52 percent) and is the second-most targeted by attacks against authentication (10 percent). This diversity of attacks indicates a complex threat landscape requiring multifaceted defense strategies.
Healthcare and personal data: The healthcare sector shows a notable percentage of bot attacks (55 percent) and attacks against authentication (6 percent). This is particularly concerning given the sensitive nature of healthcare data, making it a lucrative target for attackers.
The low-key but targeted nature of attacks in insurance: While the insurance sector may not have the highest attack ratio, it is the third most susceptible to attacks against authentication, making up 7.5 percent of all such attacks. This stat suggests a more targeted approach by cybercriminals aiming to compromise valuable customer data.
The government sector’s unique challenge: Unlike other sectors, the government vertical has a unique attack type in the top three: bad bot, making up nearly 25 percent of attacks. This could imply politically motivated cyberattacks or attempts to compromise national security.
| Industry | Most Disproportionate Attack Type |
| Banking | Programmatic Access |
| Business Services | Bot Attacks (Aggregate) |
| Consulting | Bot Attacks (Aggregate) |
| Education | Programmatic Access |
| Electronics | SQL Injection |
| Finance | Miscellaneous |
| Government | Bot Attacks (Aggregate) |
| Healthcare | Programmatic Access |
| Insurance | Bot Attacks (Aggregate) |
| Manufacturing | Error Rate |
| Media & Entertainment | Programmatic Access |
| Other | Programmatic Access |
| Professional Services | Plugin Enumeration |
| Retail & Distribution | Programmatic Access |
| Software & Technology | Directory Traversal |
| Telecomm | Bot Attacks (Aggregate) |
| Transport | Programmatic Access |
| Utilities | Customer Rule |
These disproportionate attack types indicate that different industries may be particularly vulnerable to, or targeted for, specific kinds of cyberattacks. For example:
Programmatic access is the most disproportionate attack in several verticals, including banking and healthcare. This could indicate automated or bot-driven attacks aimed at exploiting vulnerabilities in these sectors.
Bot attacks are more prevalent in government, insurance, and consulting sectors, possibly indicating a focus on data scraping or DoS attacks.
SQL injection is most disproportionate in the electronics sector, potentially revealing a vulnerability in database security for these companies.
Bot Attacks by Industry
The overall percentage of bot attacks across all industries is approximately 48.96 percent.
But there are some industries facing a higher than average number of bot attacks, including banking, education, and utilities. [Note: The education sector data is somewhat skewed due to a smaller sample size and some significant bot activity in Q3. That being said, a good reminder that education is becoming a popular attacker target due to its high amount of sensitive data, such as financial and health information.]
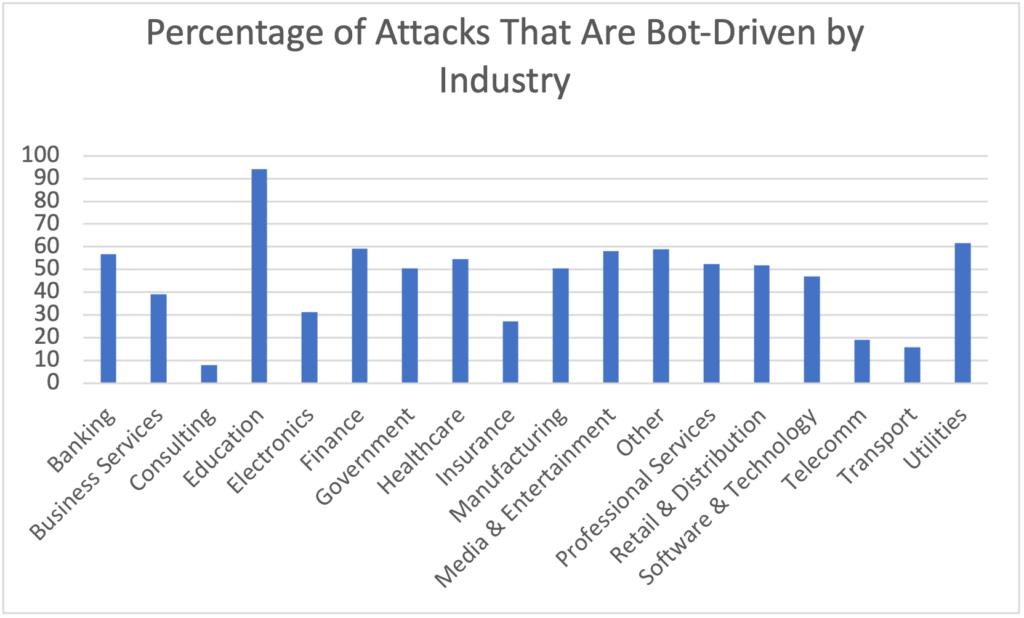
Figure 3: Bot attacks by industry
Attacks Against Authentication by Industry
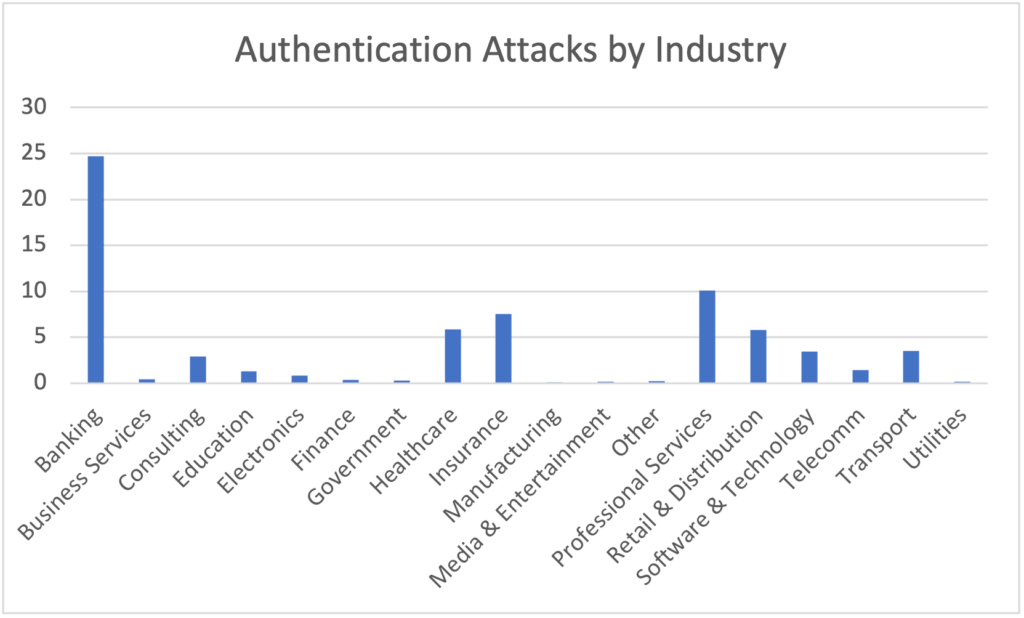
Figure 4: Authentication attacks
The banking sector stands out here with a particularly high percentage of attacks against authentication, making up nearly 25 percent of such attacks. This is followed by professional services and insurance sectors with 10.08 percent and 7.54 percent respectively. These percentages underscore the critical need for robust authentication mechanisms, like multi-factor, especially in sectors like banking.
API Traffic and Attack Analysis
API use is clearly increasing and expanding, as we found that the overall percentage of HTTP traffic that is API traffic across all industries is approximately 59.83 percent. But for some industries, like banking and retail, the use of APIs is really exploding (see Figure 5).
API Traffic by Industry
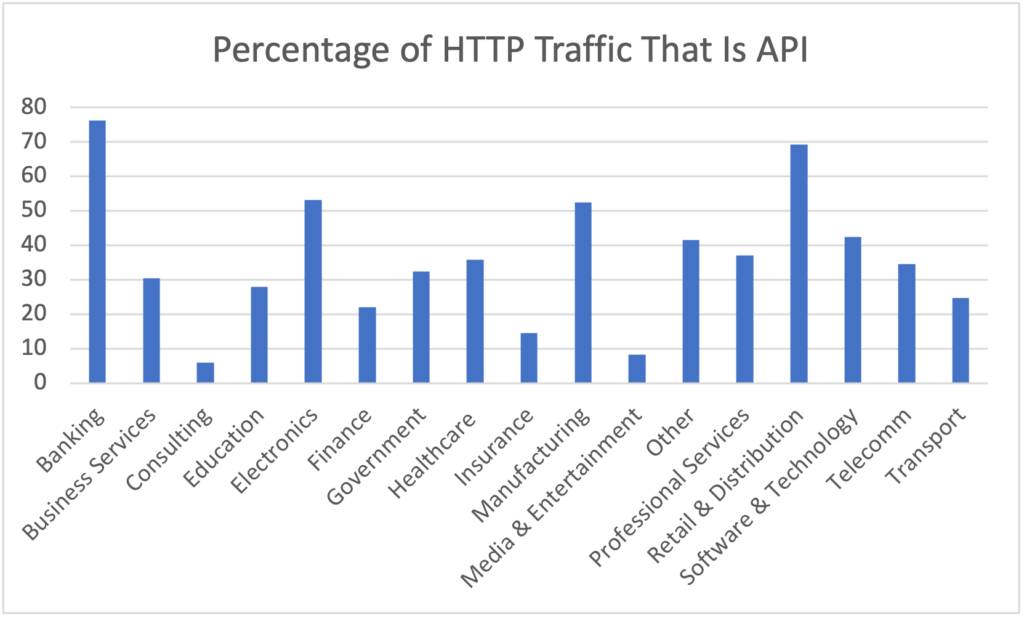
Figure 5: Percentage of API traffic
Table 2 below highlights the top attack types we see in each industry.
| Industry | Top 3 API Attack Types |
| Banking | Credential Stuffing (24.7%) Programmatic Access (21.7%) Brute Force (9.9%) |
| Business Services | Programmatic Access (38.7%) Misc (11.3%) XSS (Cross-Site Scripting) (11.2%) |
| Consulting | Directory Traversal (21.9%) Programmatic Access (17.5%) Command Injection (12.5%) |
| Education | Programmatic Access (93.9%) Password Spraying (3.7%) Traffic Flood (1.5%) |
| Electronics | Programmatic Access (30.3%) SQL Injection (14.4%) Directory Traversal (14.1%) |
| Finance | Programmatic Access (58.9%) Misc (7.1%) SQL Injection (6.6%) |
| Government | Programmatic Access (49.7%) Bad Bot (24.5%) Misc (16.7%) |
| Healthcare | Programmatic Access (48.8%) Error Rate (14.6%) Misc (13.6%) |
| Insurance | Programmatic Access (19.7%) Software Detection (19.3%) Customer Rule (18.2%) |
| Manufacturing | Programmatic Access (50.4%) Error Rate (19.8%) Toolkit (12.5%) |
| Media & Entertainment | Programmatic Access (58.0%) Plugin Enumeration (13.7%) Toolkit (11.5%) |
| Other | Programmatic Access (58.6%) Plugin Enumeration (11.4%) Error Rate (9.6%) |
| Professional Services | Programmatic Access (38.1%) Credential Stuffing (16.5%) Toolkit (10.9%) |
| Retail & Distribution | Programmatic Access (47.0%) Misc (12.3%) Error Rate (9.4%) |
| Software & Technology | Programmatic Access (43.9%) Directory Traversal (17.2%) Evasion (13.5%) |
| Telecomm | Error Rate (26.2%) Programmatic Access (24.2%) Information Disclosure (11.8%) |
| Transport | Web Attack (29.3%) SQL Injection (14.1%) Programmatic Access (12.4%) |
| Utilities | Programmatic Access (61.6%) Customer Rule (12.4%) Error Rate (11.1%) |
Definitions
Customer Rule: This represents matches to custom-defined rules within the ThreatX API and Application Protection platform.
Web Attack: An attacker uses known attack parameters or a known payload.
SQL Injection: In a SQL injection attack, an attacker injects a SQL query via the input data from the client to the application.
Information Disclosure: For example, if an error message discloses too much information and an attacker tries to get to the location of information disclosure.
Toolkit: Observation of a tool known to perform an attack.
Brute Force: Attacks that feature attackers using trial and error to try to access a system.
XSS: In a cross-site scripting (XSS) attack, an attacker injects malicious executable scripts into the code of a trusted application or website.
Bad Bot: As opposed to a good bot (such as a Google crawler).
Password Spraying: Similar to credential stuffing, but the attacker uses one user name with a variety of passwords.
Traffic Flood: A subset of DDoS; a specific use case where system performs a callback after a visit.
Command Injection: A command injection vulnerability allows attackers to execute system commands on the attacked party’s host operating system (OS).
Software Detection: Attacker getting enough access to accumulate details about software.
Plugin Enumeration: An attacker enumerating a plugin to try to gain access (typical with WordPress).
Key Takeaways
Emphasize defense against programmatic access: Given that programmatic access is significantly higher than other types of attacks, it’s crucial to implement robust anti-bot solutions and enhance user authentication and validation mechanisms.
Get more details on how attackers are leveraging bots in API attacks.
Prioritize credential defense mechanisms: Credential stuffing is prominent. Implement multi-factor authentication, monitor for suspicious login activities, and encourage users to employ strong, unique passwords.
Keep in mind that credential stuffing techniques are able to sidestep traditional WAF signatures and rate-based rules for several reasons. Most notably, the techniques do not rely on an exploit or other overt malicious action, and instead, use/abuse the exposed functionality of an application in unexpected ways.
In this case, the attacker, usually in the form of a bot, is using the application’s login functionality in much the same way that a legitimate user does.
Additionally, since attackers have many username/password combinations to cycle through, the work is typically done by a large, distributed botnet or other forms of malicious automation. This not only speeds up the work, but it allows the attacker to distribute the attack over a large number of IP addresses so that it isn’t obvious that the attack traffic is coming from a specific set of IPs.
Prevent directory traversal: Ensure secure configurations and apply necessary patches to prevent directory traversal attacks.
Examine error rates: Analyzing error rates can potentially provide insights into misconfigurations or vulnerability exploits. Keeping logs and alerts for high error rates can be pivotal for early detection of an attack.
Address evasion techniques: Consider implementing solutions that can identify and block requests trying to evade detection, such as through the use of VPNs, proxies, or other anonymization tools.
Learn more about the evasion tactics we frequently see attackers employ.
Enhance overall security posture: Even though some attacks like SQL injection and XSS are not topping the chart, they can be highly damaging. Ensure that security controls, like input validation and output encoding, are in place to mitigate such threats.
Awareness and training: Make sure to educate users about the importance of cybersecurity hygiene, such as using strong passwords and recognizing phishing attempts.
Utilize security features: Encourage users to enable and properly configure security features provided, such as MFA and security alerts.
Continuous monitoring: Continuously monitor the landscape for emerging threats and collaborate with security providers to understand and implement best practices.
Data privacy: Employ data minimization practices and ensure that data transit and storage are encrypted. This is crucial in minimizing the impact in case of a breach.
To learn more about how our solution collects these data points, take a quick, self-guided tour of the ThreatX platform.
