LAST UPDATED August 19, 2021
Application security never fails to keep us on our toes. Between the continuous evolution of application frameworks and integrations, and the advancement of human and automated attackers, security teams must always be braced for change and new challenges. On a similar vein, if the trends from 2018 continue, web application attacks will remain the most successful hacked area of the enterprise. In fact, over 60% of actual breaches occurred through web applications.*
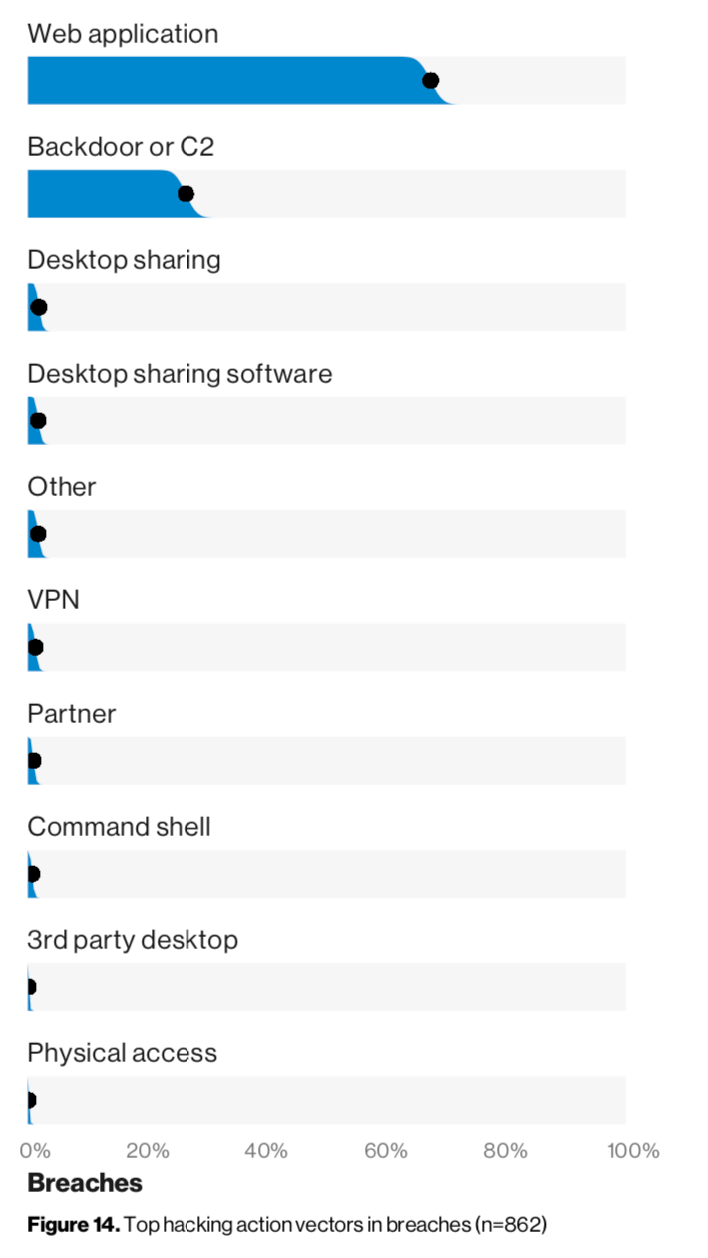
2019 Verizon Data Breach Investigations Report
Recent reports also indicate that the most common approaches to cyber attacks were stolen credentials, vulnerability exploit, and brute force, among others.* These attacks are typically executed via web applications and are often automated. This doesn’t come as a shock given that nearly 20% of all traffic to web applications comes from malicious bots.**
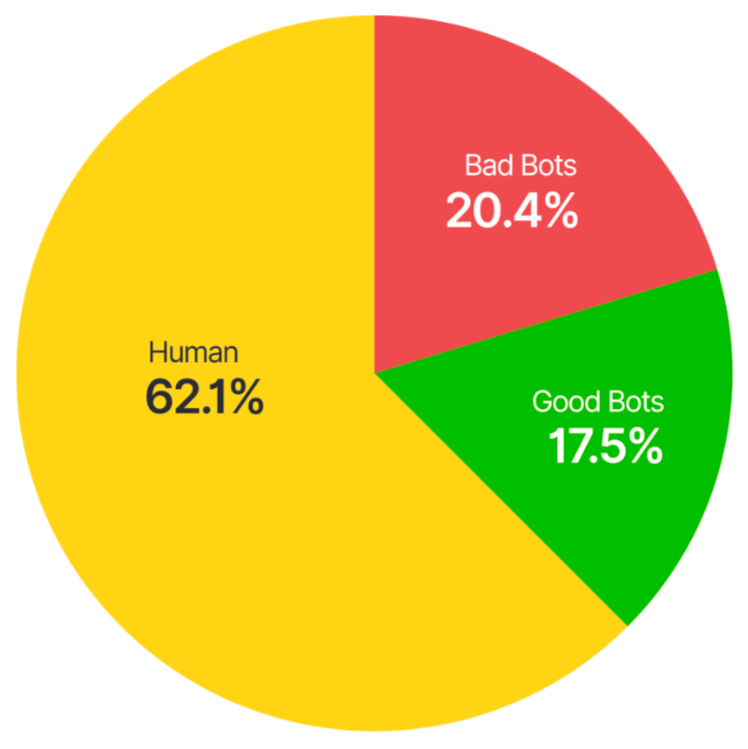
Distil Networks’ 2019 Bad Bot Report
The percentage of bad bot traffic certainly varies based on the industry, but the one thing that is certain is that no industry is immune. Therefore, it’s important that organizations are armed with data surrounding these types of attacks. With that in mind, we will take a deep dive into malicious automation, from approaches to case studies from 2019 in which a bad bot was detected and blocked. This first post will focus on the various approaches that bad bots may use, along with their intentions.
Key Characteristics of Malicious Automation
- Operate at the Application Layer
- Abuse app functionality intended for valid users. For example, logging into a website or filling out a simple user registration or feedback form. Often times, this type of behavior is layered in with automated website exploration to evade detection.
- Can coordinate large numbers of attacking nodes from different IPs. By doing so, bots can generate load and attempt different variations of one action, such as a login, in a short period of time. This capability has only been enhanced with the advent of public cloud.
- Often invisible to traditional WAFs. Many traditional AppSec tools don’t have the ability to correlate multiple IPs to the same attacker, which means these malicious bots will simply evade detection and go un-contained.
Top Motivations Behind Malicious Automation
- Data exploitation
For example, scraping competitive info, pricing, availability, etc. This type of attack is common with online retailers, hotels, and travel sites. Retailers promise to price match, right? Which explains why some items on an E-commerce site don’t provide a price until it’s in your cart. - Out-compete human users
Bots can be used to buy out inventory to then resell on secondary markets, something that’s very common with ticketing and retail. Think movie tickets, concerts, and sporting events. - Commit theft or fraud
At times bots are used to validate stolen payment cards, steal PII data, take over user accounts, and obtain loyalty points. We see this most often in the financial services, retail, and hospitality verticals. - Influence public perception
Incredibly, automations can be used to create fake reviews, cast fake votes, drum up video plays, etc., all to influence public perception. Social media, review sites, and online voting platforms are the primary victims of this type of attack.
The above findings mirror much of what we are seeing across our customer base in 2019. Say what you want about automation, but there’s no denying that threat actors are successfully leveraging it to deploy bots and launch malicious attacks.
In our next post, I’ll go through the four most common types of automated attacks that we see “in the wild,” including credential stuffing and carding. Stay tuned!
*Based on research from the 2019 Verizon Data Breach Investigations Report
**Based on research from the Distil Networks’ 2019 Bad Bot Report
