ThreatX is now a part of A10 Networks
The A10 Defend portfolio now includes ThreatX Protect cloud WAAP solution, giving customers an additional tool in their strategy to protect against new and evolving threats.
Read the NewsSecure APIs & Apps with Real-Time Visibility and Protection
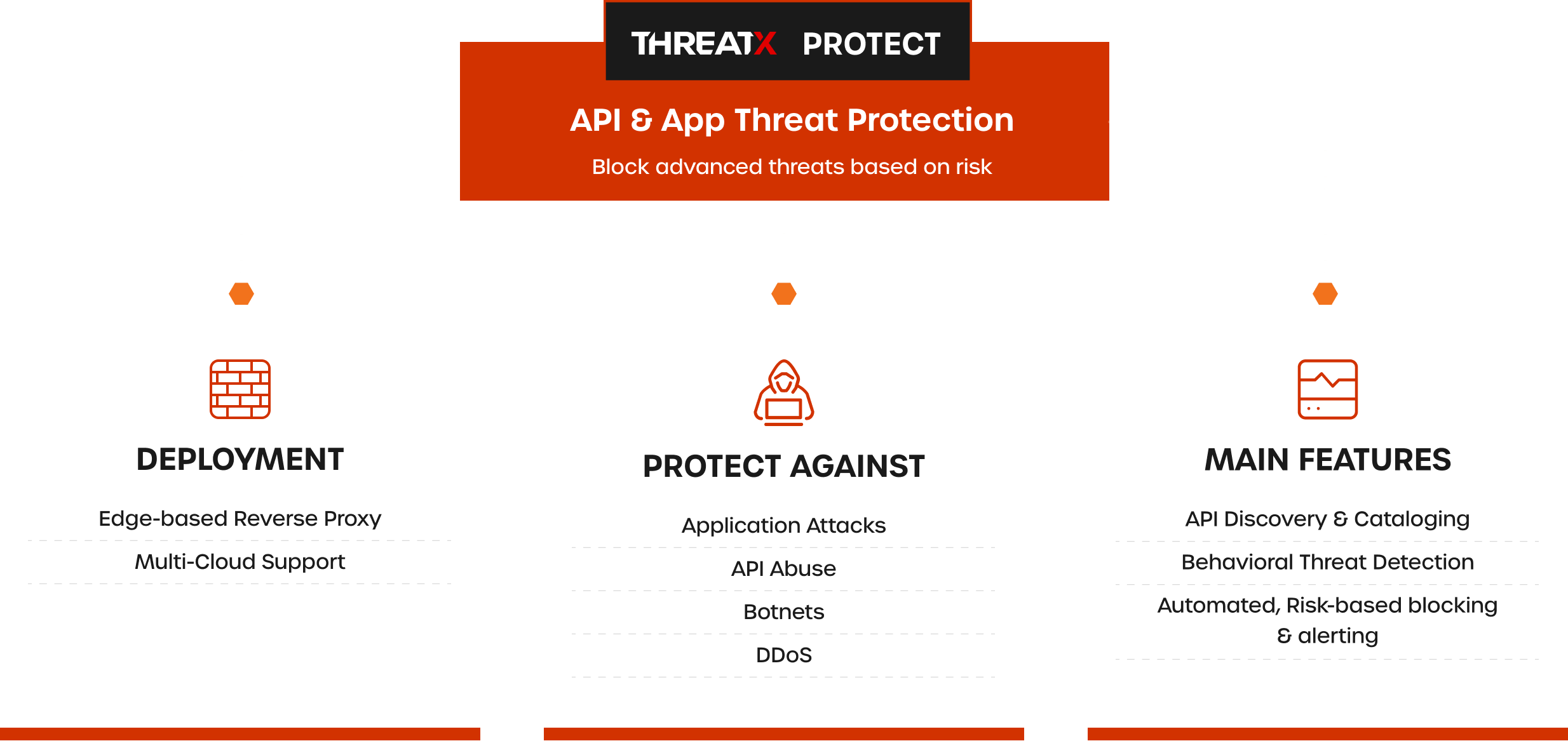
Learn how ThreatX by A10 Networks can augment your API and application security efforts.
Eliminate Risks Without Compromising Your Time Or Peace of Mind

Before
After
Easy-to-Use
- Complex deployments and multiple integrations required
- Alert-heavy systems that require manual intervention and investigation
- Fragmented dashboards that don’t tell a clear story or prioritize risks
- Reverse-proxy deployments supported by experts
- 24×7 Active Monitoring with by our Security-as-a-Service team
- Easily investigate high risk threats with simplified dashboards
Easy-to-Manage
- Multiple point solutions for apps, APIs, and bots
- High false-positive rate with rule & signature-based detection
- Heavy manual investigation required before response
- One platform for apps, APIs, and bots
- Efficient & effective threat detection based on behavior
- Reduce manual work by automating responses for threats
Eliminate Risks
- Signature & IP-based blocking that doesn’t keep attackers out, generating false positives, and requires constant tuning
- Stop attackers effortlessly with automated, risk-based blocking
Product Features
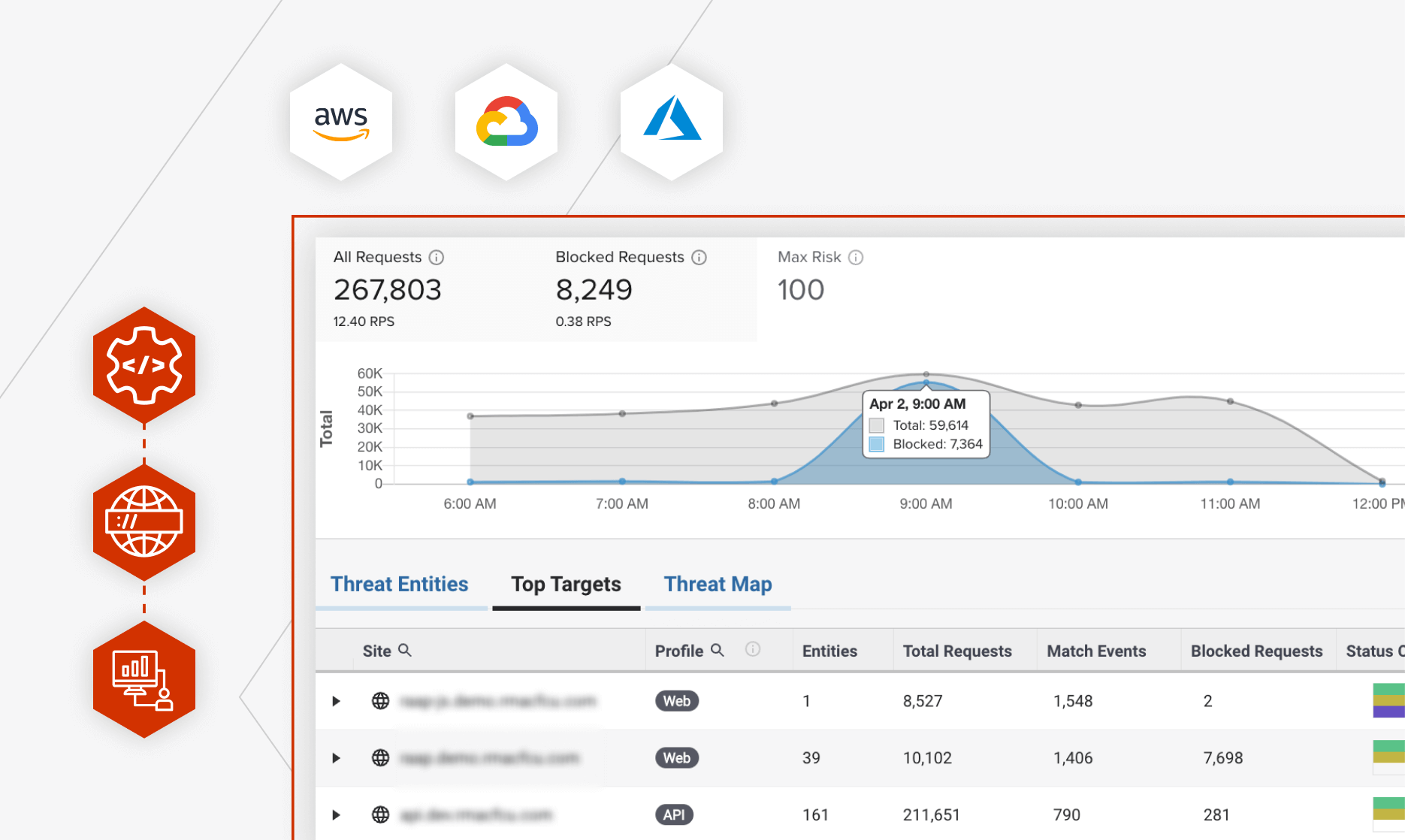
Real-time Visibility at the Edge
Monitor API and web application traffic at the perimeter in real-time. Manage active sites and discover which endpoints are top targets.
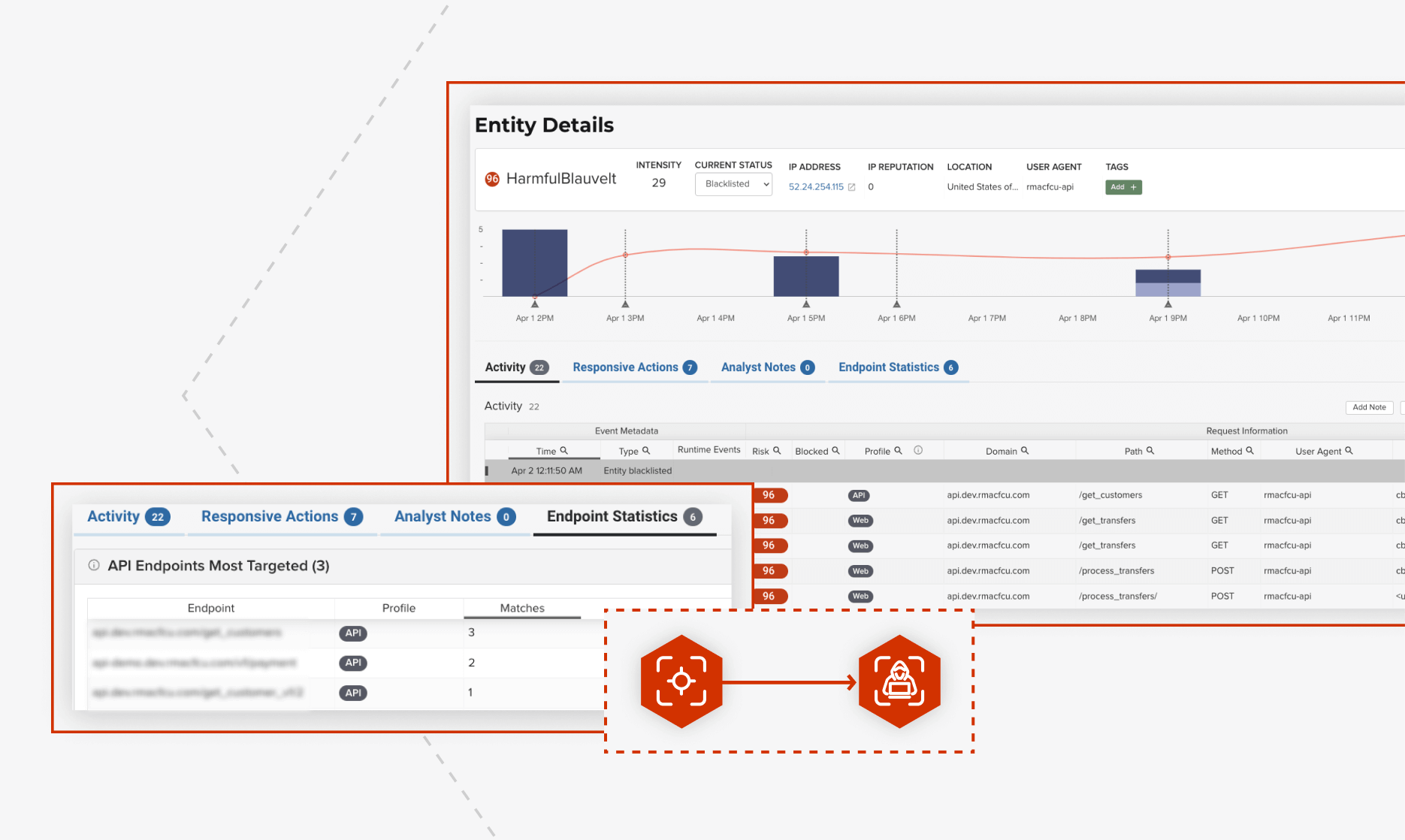
Behavioral Threat Detection
Detect malicious activity, track their behavior over time. See which websites and APIs are being targeted.
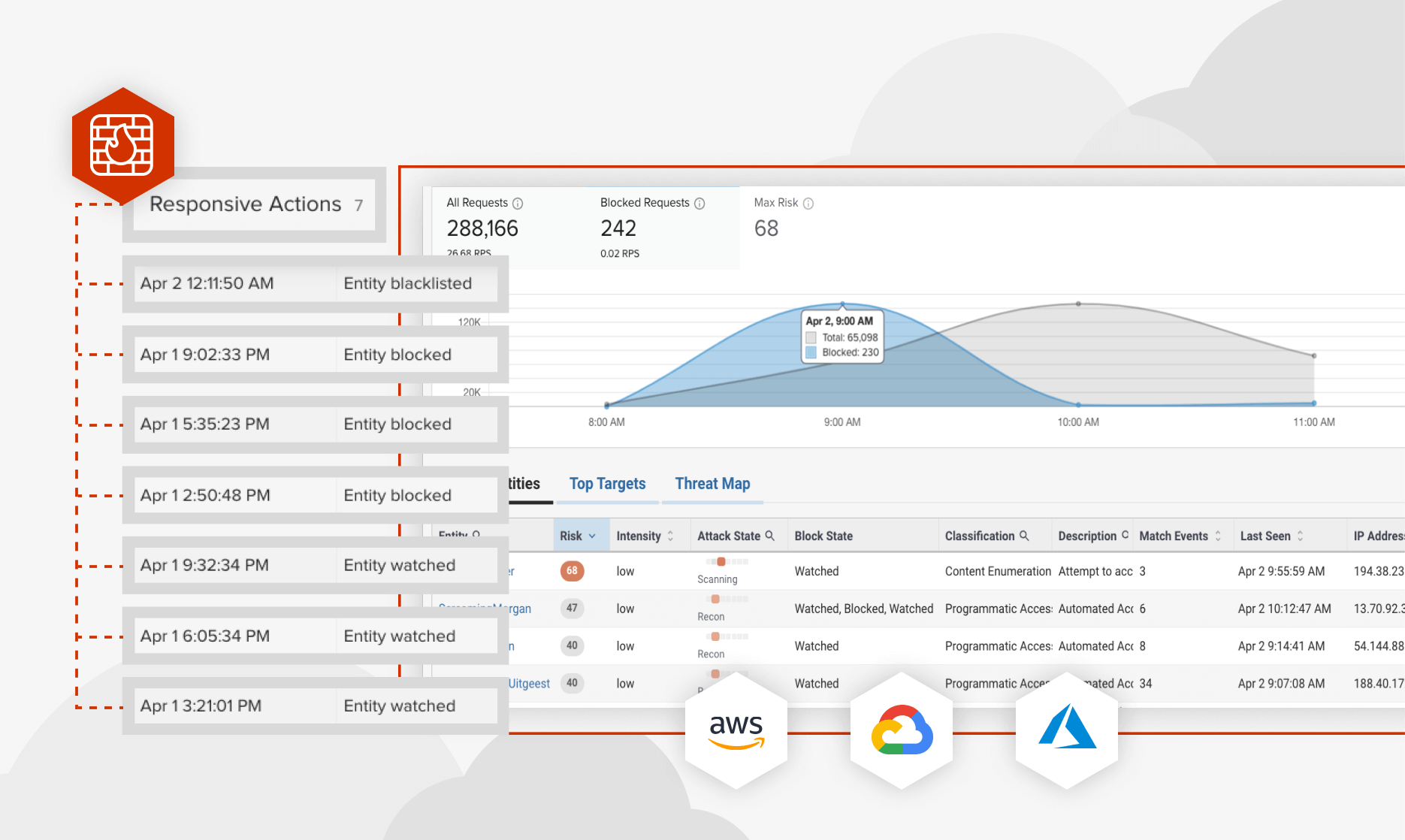
Automated, Threat Protection
Automatically respond to threats based on risk by tar-pitting, blocking, or alerting your teams. Stop known bad actors without any manual intervention required with risk-based protection.







